SYDNEY J. FREEDBERG JR.

WASHINGTON – Zero trust, but verify: That’s the strategy the Pentagon is experimenting with for its new private-sector cloud providers.
Beginning this spring, red-team hackers from the National Security Agency — and possibly the armed services’ red teams as well — will launch a months-long series of attacks on zero-trust security systems on clouds run by Amazon Web Services, Google, Microsoft and Oracle, according to the head of the Defense Department’s zero-trust office.
“That would be a realistic adversary attack [to] determine whether or not the red teams could get in and exploit data,” Randy Resnick, chief of the Zero Trust Portfolio Management Office, told a Billington Cybersecurity webcast this afternoon. “That’s going to give us a really good feel on whether or not these zero trust overlays are implemented correctly.”
It will also “give us a way forward for recommending to the DoD whether or not we could do zero trust in the cloud,” he said. “If … we come to the conclusion that in fact it can be done, it would be absolutely revolutionary.”
Why those four firms? They just happen to be the ones announced on Dec. 7 as the winners of the long-awaited Joint Warfighting Cloud Capability (JWCC) contract, itself a successor to the failed JEDI program.
“We saw that there were four CSPs, or cloud service providers, that were delivering services in the future under the JWCC contract,” Resnick explained, “and so we said to ourselves, ‘Why don’t we approach those four contractors — independent of JWCC — but to bring up the subject of zero trust with them, show them what our definition of zero trust is… and ask them whether or not they believe they can do zero trust to the target level within their cloud infrastructures.”
Randy Resnick (DoD CIO photo)
It’s important to understand this was a request, not a mandate, and that compliance with Resnick’s zero-trust standards is not a requirement of the JWCC contract itself. Instead, this is an experiment to see how quickly high-end commercial CSPs can implement those standards, set by the Pentagon’s Zero Trust Strategy [PDF]. That’s a five-year plan produced by Resnick’s office to move military networks from their current reliance on perimeter defense, where everyone who makes it past the firewall has full access, to defense-in-depth, where every user’s actions and credentials are continually monitored and double-checked.
Resnick is confident they can, at least to the basic “Target” level, which requires 91 specified protections. One or more of the four vendors may well reach the more demanding “Advanced” level, which requires an additional 61.
“They said to us that all of them could meet ‘Target’-level zero trust,” Resnick said. “Many of them could approach almost the entirety, if not the entirety, of full zero trust.”
But that’s “on paper,” Resnick emphasized. He wants them to prove it.
“What we plan on doing is actually testing their assertions,” he said. “So this year in the spring and summer — perhaps fall, depending on whether or not we have to go back for round two — we’re intending on testing all four of those CSPs.”
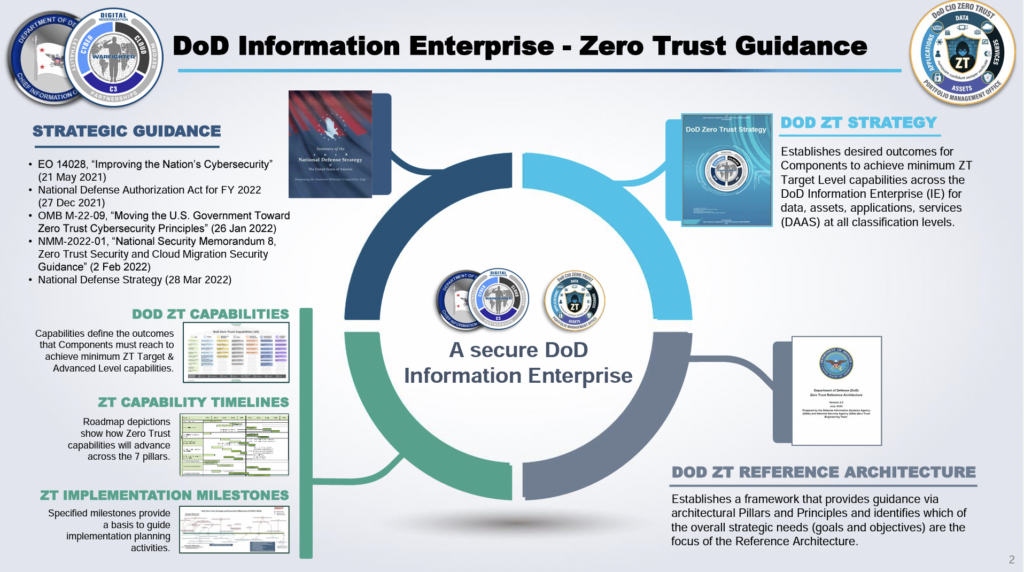
Overview of the Pentagon’s 2022 Zero Trust Strategy (DoD CIO graphic)
“We’re going to have the NSA red team, and perhaps even service red teams, attack that,” he said.
Why? Because instead of the Pentagon having to laboriously build zero-trust clouds on its own, or wait for the private sector to layer zero trust protocols on existing services, the military could simply buy cloud services off the shelf — for example, under the JWCC contract — and have full confidence that zero trust protections were built in.
“It would already be built in with zero trust as part of its foundation,” Resnick enthused. “You would still have to write the rules, the policies, you know, the user-end of things, but the hard work of putting it all together and integrating all those capabilities that we’re talking about in the strategy would already be pretty much pre-done for you.
“That is a dramatic change in implementing zero trust,” he said. “It reduces risk. It reduces cost. It greatly simplifies moving to zero trust for the department.”
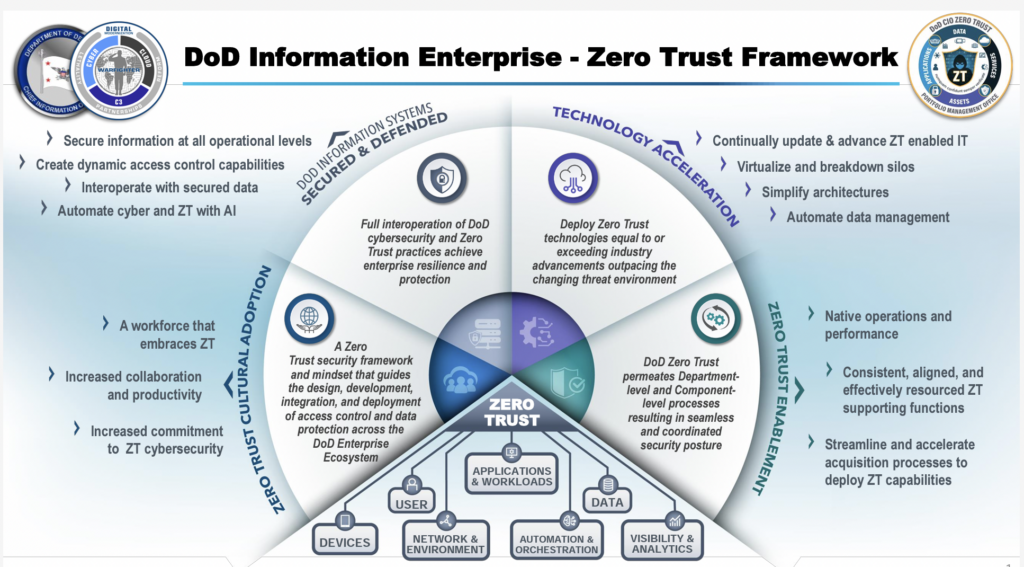
Overview of the Pentagon’s 2022 Zero Trust Strategy (DoD CIO graphic)
In parallel to red team testing the four private-sector CSPs, Resnick added, NSA will also red team the government-developed Native Zero Trust Cloud (NZTC), part of US Cyber Command’s DreamPort initiative. NZTC should be able to meet the full requirements for the “Advanced” level of zero-trust protection, giving DoD an in-house alternative cloud with the highest level of security.
The objective is to give the armed services, defense agencies and other DoD organizations a wealth of choices, not a straitjacket, Resnick said. Some mission-critical functions may never be able to move to the cloud at all, he said. In those cases, zero-trust protections will have to be grafted on to existing on-premise systems, a laborious process that Resnick expects will take until 2027. “That’s why we have the five year plan,” he said.
Upgrading existing DoD systems to zero trust is what Resnick’s Strategy & Roadmap calls “Course of Action 1.” COA 2 is buying zero-trust cloud services off the shelf from the private sector, most obviously through JWCC, but also through other vehicles from other vendors as well. And finally COA 3 calls for zero-trust clouds built and operated by DoD itself, like CYBERCOM’s NZTC.
“We’re expecting that the services are going to have any combination of COAs one, two, and three, because they’re going to have to look at each one of the networks [they now use],” Resnick said. There’s no one-size-fits-all solution, he emphasized: “We’re giving them the maximum flexible options.”
No comments:
Post a Comment