JUSTIN KATZ
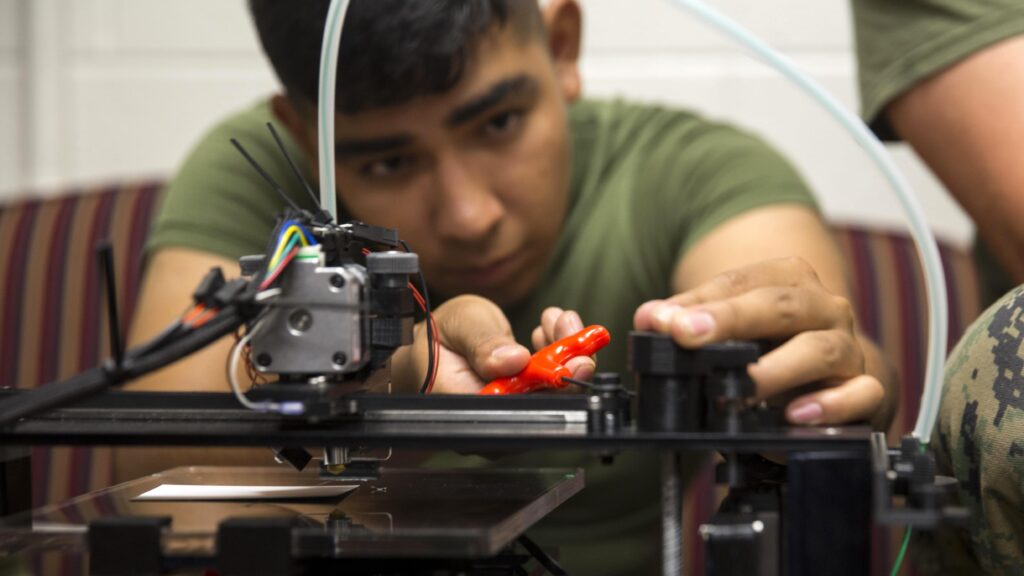
WASHINGTON: A Pentagon watchdog is raising the alarm about the military’s prolonged exploration into 3D printing, after discovering officials at several agencies are failing to manage crucial cybersecurity controls necessary for operating the technology safely.
As a result, Defense Department components working with the technology, formally known as additive manufacturing, are “unaware of existing AM system vulnerabilities that exposed the DoD Information Network to unnecessary cybersecurity risks,” according to a new report published by the Defense Department inspector general today.
“The compromise of AM design data could allow an adversary to re-create and use DoD’s technology to the adversary’s advantage on the battlefield. In addition, if malicious actors change the AM design data, the changes could affect the end strength and utility of the 3D-printed products,” the report continued.
Auditors initially selected nine agencies across the services to include in their report; however, the stop movement order issued at the outset of the coronavirus pandemic forced the inspector general’s office to reduce their sample size to five. The agencies evaluated in the report include the 1st Marine Expeditionary Force, the Navy Fleet Readiness Center Southwest, Naval Information Warfare Center Pacific, the Air Force 60th Maintenance Group and Walter Reed National Military Medical Center.
The collision of the military’s cybersecurity practices and additive manufacturing is one long in the making.
Third party watchdogs for years have dogged the Pentagon for its failures to prioritize cybersecurity upfront in the acquisition process. The entire federal government’s cybersecurity efforts – or lack thereof – are now under heavy scrutiny after attacks on firms such as SolarWinds, Microsoft and, most recently, the software company Kaseya, have opened pathways into federal networks.
Meanwhile, the military services have been eager to tout their advances in additive manufacturing. Marine Corps officials regularly praise an enlisted servicemember in California who saved countless dollars and time after designing a 3D-printed tank impellor. As Breaking Defense reported last year, the Army is interested in what parts from a Black Hawk helicopter could be produced through additive manufacturing. And the former Air Force acquisition executive Will Roper promised his service would “have a space-based challenge coming soon” during an advanced manufacturing competition hosted in October, Breaking Defense also reported.
The list of examples goes on, but what the DoD IG made clear in its report is that military personnel are viewing additive manufacturing devices as “tools” to supply parts, rather than a piece of information technology susceptible to an attack.
“In addition, the DoD Components incorrectly categorized the AM systems as stand-alone systems and erroneously concluded that the systems did not require an authority to operate,” according to the IG.
The audit included 73 printers and 46 computers and was grounded by the National Institute of Standards and Technology’s Special Publication 800-53 – the federal government’s go-to manual for cybersecurity controls.
The report lists off seven basic controls that NIST recommends but redacted the specific measures that certain installations were failing to enforce. The watchdog credited officials generally for making changes following auditor visits, but also found installations were making similar – and serious – mistakes, such as failing to update computer operating systems.
“The need to update operating systems is critical to protecting the AM computers and the printers connected to them. For example, in 2019, Microsoft issued over 197 operating system updates to fix security vulnerabilities, one of which fixed a vulnerability that allowed attackers to gain unauthorized access to a single computer and then use that access to log into other computers,” according to the IG report.
The IG’s recommendations largely focused on clarifying the policies surrounding additive manufacturing to make clear it must be treated as any piece of IT would be. The installations largely agreed with the watchdog’s suggestions.
The sole disagreements came from the DoD chief information officer, who contended the military’s policies around cybersecurity included 3D printing technology. The IG acknowledged those disagreements but still deemed the recommendation resolved because the changes the DoD CIO did commit to making “meet the intent of the recommendation.”
No comments:
Post a Comment