By THERESA HITCHENS
NC3 network, Office of the Deputy Assistant Secretary of Defense for Nuclear Matters
 WASHINGTON: A classified assessment of America’s nuclear command, control and communications system (NC3) has rung alarm bells on Capitol Hill. The assessment was mentioned in a provision crafted by the Senate Armed Services Committee for the 2021 National Defense Authorization Act and accepted by the House in their conference deliberations.
WASHINGTON: A classified assessment of America’s nuclear command, control and communications system (NC3) has rung alarm bells on Capitol Hill. The assessment was mentioned in a provision crafted by the Senate Armed Services Committee for the 2021 National Defense Authorization Act and accepted by the House in their conference deliberations.The Secretary of Defense to submit to the congressional defense committees a plan, including a schedule and resourcing plan, to implement the findings and recommendations of the first annual assessment of cyber resiliency of the nuclear command and control (NC3) system. The provision would require the Secretary to develop a concept of operations to defend the NC3 system from cyber attacks and develop an oversight mechanism to ensure implementation.”
The NDAA bill’s text elaborates that, besides a CONOPS plan, the DoD report must detail the division of roles and responsibilities among the Office of Secretary of Defense, the combatant commands, the military services, DoD agencies and field services when it comes to nuclear command and control. Congress also wants specifics on “cybersecurity capabilities to be acquired and employed and operational tactics, techniques, and procedures, including cyber protection team and sensor deployment strategies, to be used to monitor, defend, and mitigate vulnerabilities in nuclear command and control systems.”
A SASC spokesperson declined to comment on the issue today, citing its classified nature. A Strategic Command spokesperson said they are unable to comment. The House passed the conference bill on Tuesday; the Senate passed the bill this afternoon. We tried a number of other sources knowledgeable about these concerns and all declined to speak.
The classified assessment piquing congressional concern was required under Title 10, Sec. 499, which stems from language in the 2018 defense appropriations bill passed by Congress Dec. 12, 2017. The law requires an annual report.
Some hints can be found in the 2019 cyber resiliency report by the Office of Test and Evaluation (DOT&E). The report mentions a special classified review of NC3 systems done at the request of STRATCOM, the DoD Chief Information Officer and the Defense Threat Reduction Agency. The review was designed to “characterize the status and identify options for improving the mission assurance and cyber-related aspects of the NC3 capability. The results of these assessments were briefed to the highest levels of DOD leadership and have resulted in a significant increase in focus in this vital area. (emphasis added)”
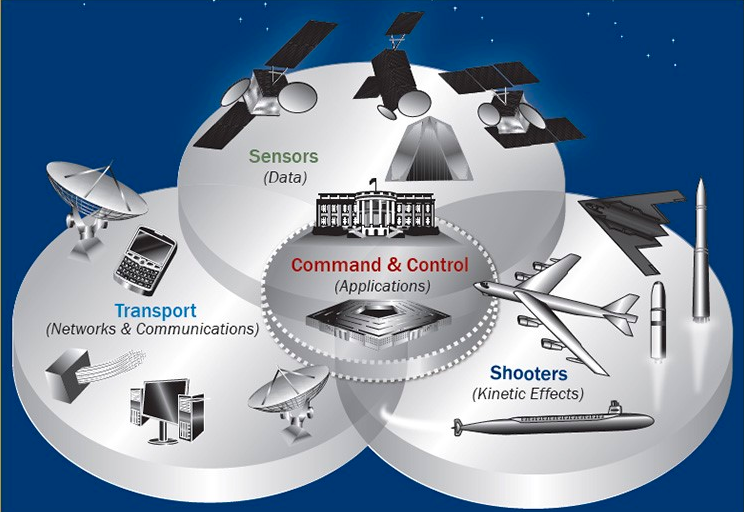
The congressional action comes as the Air Force and STRATCOM are pushing to speedily modernize NC3 capabilities. As Breaking D readers know, work on NC3 and All Domain Operations is occurring in parallel, with the nuclear and non-nuclear sides of the military sharing lessons. Allowing a normally closed system like nuclear command and control to be linked to versions of the Internet offers benefits and risks.
“Simple updates to hardware, old and new, are not enough. NC3 Next represents the future for ensuring that the president the United States has uninterrupted command and control with their forces,” Air Force Lt. Gen. James Dawkins, deputy chief of staff for strategic deterrence and nuclear integration, told the Nuclear Triad Symposium yesterday. “We’ve got to have an NC3 Enterprise Architecture that provides NC2 over assured comms for seamless integration of conventional and nuclear forces,” he said. He repeated the phrase twice for emphasis.
NC3 is often hard to explain, Dawkins admitted, not just because it is inherently technical but also because of secrecy. The “nuclear priesthood” are sometimes their own worst enemies, talking in a kind of coded language based on acronyms. NC3, he said, simply “comprises command, control communication systems that link the president and national leaders to the force.” Whereas NC2, by contrast, is “the authority and the processes we use to get messages and direction out of the force.
Lt. Gen. James Dawkins (left)
“For most conventional operations, we delegate released authorities down several levels, we can accept some lack of connectivity, or spotty connectivity in the C2 architecture,” Dawkins said. “But this is not the case with NC2. So, we have to establish specific, hardened architectures and systems to ensure connectivity in the worst case on the worst day. This is often referred to by the NC3 community as the ‘thin line.’ Think of it as the last line of communication capabilities and associated equipment that we know will always be there during our worst day.”
At its most basic, he explained, NC3 consists of “radios or terminals that enable command authorities to receive information and pass messages to the operators to do a specific action. … And these terminals operate across various waveforms or pathways, whether it’s ultra high frequency or UHF, very low frequency VLF, or high frequency, also called HF. And these waveforms and pathways are really a mix of unhardened and hardened — unencrypted and encrypted — systems. So, yes, it’s complex.”
Those radios and terminals are embedded into some 62 different systems — from satellites such as the Advanced Extremely High Frequency (AEHF) for encrypted strategic communications to nuclear submarines to the E-4B National Airborne Operations Center (NAOC) aircraft known as the “Doomsday” planes. Most of those systems are ancient in information technology years, with many dating back to the 1980s pre-Internet era.
The details of the NC3 Next effort, which got a strong push from Vice Chairman of the Joint Chiefs of Staff Gen. John Hyten when he led STRATCOM, are mostly classified.
Dawkins said NC3 Next could be thought of as “the ‘to be’ architecture; the ‘to be’ systems. When realized, NC3 Next will maintain and improve on the readiness and reliability of today, while also dealing with new threats from our potential adversaries.” The goal is not “merely recapitalize along the lines of what we’ve been doing,” he elaborated, rather “to implement entirely new technologies concepts and methods for achieving dynamic and assured connectivity that can meet evolving nuclear mission requirements.”
The idea, Dawkins added, is similar to what is happening under the Joint All-Domain Command and Control (JADC2) initiative to link all sensors to all shooters, and the Air Force’s tech program for enabling it, the Advanced Battle Management System (ABMS). “As such, NC3 Next and JADC2 must be linked,” he said, echoing what Hyten told Breaking D in an exclusive interview in February.
“We’ve got to look for similarities and differences that similarities of NC3 and NC2 with JADC2 and ABMS, and then carve out the differences,” Dawkins added. “We’ve got to leverage the similarities and make exceptions for the differences.”
The budget for NC3 Next is classified, although a Congressional Budget Office study last year said it could be as much as $77 billion. Just one effort, the Air Force’s program to recapitalize the four Doomsday planes, is budgeted at $634.6 million through 2025 — although, as colleague Valeria Insinna first reported, the service has delayed its plans to issue a request for proposals this month to launch the upgrade as it ponders a new acquisition strategy.
Meanwhile the Air Force has a near-term set of related improvements underway for its bomber fleet, Dawkins said. One ongoing line of effort is to improve the communications capabilities of the B-52 bombers, including a new EHF terminal “that will provide resilient and robust beyond-line-of-sight connectivity into the 2030s,” he said. It also includes an effort with the Navy to improve VLF communications with submarines.
“These programs must stay on track,” he stressed, “in order to keep our current force relevant in the face of evolving sophisticated threats.”

No comments:
Post a Comment