By SYDNEY J. FREEDBERG JR.
 WASHINGTON: Agencies from across the Defense Department are coming together to turn zero trust from buzzword to reality. Led by the Defense Information Systems Agency (DISA) and the National Security Agency (NSA), the workshops’ goal is to create a set of “best practices” to guide upgrades across DoD, said Vice Adm. Nancy Norton. Norton commands both DISA, the Pentagon’s tech support agency, and JHFQ-DoDIN, the DOD’s operational HQ for day-to-day cybersecurity.
WASHINGTON: Agencies from across the Defense Department are coming together to turn zero trust from buzzword to reality. Led by the Defense Information Systems Agency (DISA) and the National Security Agency (NSA), the workshops’ goal is to create a set of “best practices” to guide upgrades across DoD, said Vice Adm. Nancy Norton. Norton commands both DISA, the Pentagon’s tech support agency, and JHFQ-DoDIN, the DOD’s operational HQ for day-to-day cybersecurity.
“The initial Zero Trust Reference Architecture … will be out towards the end of this year,” Norton told AFCEA’s annual Army Signal conference this morning. While lots of companies are eager to sell products labeled “zero trust,” the architecture is intended to show Defense Department organizations how they can upgrade the technology they already have.
That means converting systems that now rely on a single line of defense to a layered defense based on zero trust. Most current information technology – including countless aging systems in the Defense Department – relies on perimeter security, where logging in means you can access all the data on a given device or even a whole network. But cybersecurity experts assume these days that the enemy will get through that perimeter – or be already inside it with legitimate credentials, as Ed Snowden was at NSA. So zero trust constantly checks and re-checks each user and software process each time they try to access data, operating under the principle of “deny by default.” You don’t get access unless you specifically prove you should have it.
The standard analogy is a castle with a moat. Perimeter security checks visitors at the drawbridge and then gives them free run of the castle, while zero trust posts guards at every chamber.
That’s a huge change, requiring a complex kit of analytic software, identification and verification systems, and bureaucratic policies. But the Pentagon can’t afford to rip out its entire IT system and buy a replacement.
“We very much understand that this is not going to be a wholesale, green-field approach to new network architecture,” Norton said. “We’re not starting over again [buying] wholesale new equipment. We are taking what’s out there today with our legacy equipment and… incorporating new principles and new analytics and specific kinds of policies… adding devices and automation into the architecture that we already have.”
Since the plan is to add zero trust to existing systems, DISA and NSA need to understand how those systems work. Hence the workshops they’re conducting with other agencies, from roughly quarterly meetings of top officials down to more frequent conclaves at the working level.
“The workshops are going really well and we’re getting lots of participation,” Norton said. “There is definitely a lot of interest in there.”
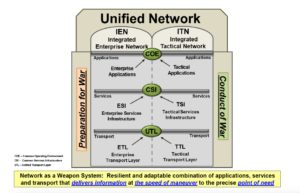
The Army’s plan to integrate its enterprise (homebase) and tactical (battlefield) networks.
Ambivalence in the Army
 The Army’s chief information officer, Lt. Gen. Bruce Crawford, has been particularly enthusiastic and ahead of the curve, Adm. Norton told an Army-heavy audience at AFCEA.
The Army’s chief information officer, Lt. Gen. Bruce Crawford, has been particularly enthusiastic and ahead of the curve, Adm. Norton told an Army-heavy audience at AFCEA.
“The Army very definitely has from the beginning said, ‘we want to be part of zero trust,’” Norton said. “Gen. Crawford was … pushing, actually, DISA [to] move to a zero trust environment.”
The Army’s Network Enterprise Technology Command (NETCOM) is already working on a zero trust pilot project with Norton’s JFHQ-DODIN, NETCOM’s chief engineer told the AFCEA conference. “A few months ago [US Cyber Command] asked each of the services to conduct a zero-trust pilot,” Patrick Dedham said. “We stood up a team that’s actually trying to implement a zero-trust environment using a [Microsoft] 365 environment.”
As with the DISA-led, DoD-wide effort, the NETCOM pilot is focused on the nitty-grity of implementing zero trust in existing technology, not some grand plan to rip everything out and replace it with shiny new stuff. “As we go through that pilot and discover what does it really mean to implement zero trust principles on our network today, then that’ll allow us to come up with a much better architecture,” Dedham said. “Zero trust is going to be a journey…Right now we’re very perimeter-security-based.”
As hard as it is to implement zero trust in the Defense Department’s “enterprise” networks – which are largely based in the US with easy access to fiber optic landlines – it might take even longer to implement in the tactical units that units deploy with, which largely depend on radio and which must work alongside foreign allies.
Maj. Gen. Peter Gallagher
 “We have to connect with coalition teammates, okay? We absolutely have to,” said Maj. Gen. Peter Gallagher, who leads the network modernization team at Army Futures Command. “We use terms like zero trust and identity management and all that stuff, [but in a combat zone] you can’t necessarily confirm the security clearance of everyone you’re sharing information with.
“We have to connect with coalition teammates, okay? We absolutely have to,” said Maj. Gen. Peter Gallagher, who leads the network modernization team at Army Futures Command. “We use terms like zero trust and identity management and all that stuff, [but in a combat zone] you can’t necessarily confirm the security clearance of everyone you’re sharing information with.
“There’s always a fine line between security and operational effectiveness… the ability to command and control and fight as a coalition,” Gallagher said. Indeed, one of the biggest decisions the Army has made about its future tactical network is to keep as much data as possible unclassified because it streamlines information-sharing — not just with allies but even with other US units.
Properly implemented, zero trust could make it easier to share data across a coalition, said Paul Puckett, who heads the Army CIO’s nine-month-old Enterprise Cloud Management Office. Perimeter security often required you have to have one network for all the US users and another, separate and unequal, for non-US users. But with zero trust, you can have a single network that manages individual users and their access in a much more nuanced way. Every user, device, and piece of data gets labeled with metadata attributes that clearly describe its identity and what it’s allowed to connect with, he said, “whether they’re a US person or not, whether they have clearances or not.”
Gallagher is watching this work on zero trust with interest – but considerable caution. “We’re going to have to … follow where NETCOM goes,” Gallagher told the conference, “because we’ve got to get the enterprise set first, and do it right, before we’re going to be able to really capitalize on it in the tactical space.”
No comments:
Post a Comment