 Many universities are starting to include cybersecurity as a course of study. While there is a high degree of variation between the selected readings of the syllabi of cybersecurity courses across different universities, there is some thematic overlap. By reviewing the syllabi of university cybersecurity courses, the authors seek to systematically evaluate this nascent field and advance its maturity.
Many universities are starting to include cybersecurity as a course of study. While there is a high degree of variation between the selected readings of the syllabi of cybersecurity courses across different universities, there is some thematic overlap. By reviewing the syllabi of university cybersecurity courses, the authors seek to systematically evaluate this nascent field and advance its maturity.
Dr. Max Smeets is a senior researcher at ETH Center for Security Studies and affiliate at Stanford University CISAC.
Cybersecurity is of increasing importance to societies around the world. This is reflected in national debates, where news stories about breaches, attacks, and policy challenges find their way into the headlines nearly every day. It is also reflected in the curricula of colleges and universities; many are starting to include cybersecurity as an explicit course of study.
As cybersecurity is still a maturing topic for the education community, it is prudent and timely to evaluate the state of cybersecurity instruction in political science and discuss how to improve it. To undertake this task, our forthcoming article in the Journal of Political Science Education examines patterns and variations in the content of syllabi on cybersecurity courses within political science, looking across campuses to understand the relative balance of policy topics, technical concepts, and theoretical debates in how courses are structured and presented.
Our review included thirty-two syllabi whose main focus is on cyber conflict, cyberwarfare, cybersecurity, or offensive cyber operations and discusses in depth our review criteria and other syllabi not included in the study. Twenty-seven of the thirty-two syllabi were from the United States. The five exceptions included several courses on cybersecurity and international relations at King's College London and Charles University, governance of cybersecurity at Leiden University, and cyberwarfare at the University of Nicosia.
Main finding: Few courses overlap in using the same readings—there is tremendous intellectual and disciplinary diversity in course content.
This diversity defies an easy categorization of the ‘canonical’ or core literature of the field of cyber conflict scholarship. Rather, the field is scattered across a disparate range of topics and disciplines. Of the top thirteen readings across the surveyed syllabi, all but two were published in the last seven years. These results are a remarkable contrast with other fields, including international relations, which exhibit a clear and relatively consistent core literature.
Sub-finding 1: While readings vary, there is some overlap in central themes.
Most syllabi include at least one week of coursework on cyberwarfare. Cyber power, espionage and intelligence, and China were the three most popular topics, each occurring in nearly 60 percent of our reviewed syllabi. As Figure 1 below shows, Russian cyber activity received slightly less attention.
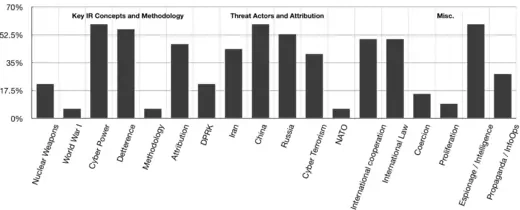
Figure 1. Central Themes in Course Syllabi
Sub-finding 2: Syllabi vary significantly in how they rely on non-academic sources.
Even though we do not have comparative data from other fields of study, there appears to be a relatively heavy reliance on literature from media outlets. Less than half of the readings assigned are academic publications (47.2 percent). Combined, news reports (15.9 percent) and government and policy reports (15.9 percent) make up just below one third of the reading on syllabi. Think tank publications and specialized blogs account for another 9.8 percent. Notably, just below 3.4 percent of syllabi rely on reports from cybersecurity firms and other companies. Of these, most only include two reports: Mandiant’s report on APT1 and Ralph Langer’s report on Stuxnet. A more detailed overview of type of readings across syllabi can be found in Figure 2.
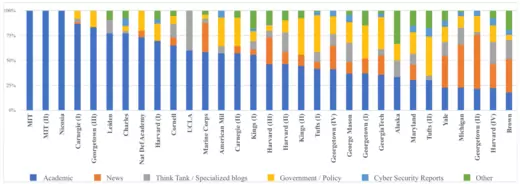
Figure 2. Types of Readings in Syllabi
Sub-finding 3: Across all of these syllabi, there is little discussion of methodology.
Only 6 percent of the syllabi explicitly discussed methodology questions in relation to studying cyber conflict. This is not entirely surprising; explicit discussions of research design in academic cyber articles are scarce. The lack of methodology discussion may also owe to the academic level of syllabi examined; the bulk are for undergraduate and masters courses. Some courses start with conceptual clarification, an initial discussion of what cyberspace is, for instance, but this varies between technical underpinnings, like the internet’s design and core protocols, and philosophical or ideological discussions, like John Perry Barlow’s “Declaration of Independence for Cyberspace.”
While cyber conflict as an academic discipline does not yet have the characteristics of a coherent field of study, its varied topics have only grown in importance and public attention in the past decade. This growth has had a delayed impact on academia, but nevertheless each year brings new courses and syllabi. Our review is an attempt to systematically evaluate this nascent field and advance its maturity—not just as an area of research but also as an area of education.
No comments:
Post a Comment