Kate Fazzini
 The Kingdom and oil and gas industry have been slow to shore up defenses, raising red flags about the possibility of longer term fallout in the region, experts said, including those who have responded to incidents in the region.
The Kingdom and oil and gas industry have been slow to shore up defenses, raising red flags about the possibility of longer term fallout in the region, experts said, including those who have responded to incidents in the region.
Investors should be wary of a long-term possibility of cyber espionage and flare-ups of malicious activity, including the potential for destructive attacks that hurt the value of companies in the region beyond Aramco.
udi defence ministry spokesman Colonel Turki Al-Malik displays on a screen drones which Saudi government says attacked an Aramco oil facility, during a news conference in Riyadh, Saudi Arabia September 18, 2019.
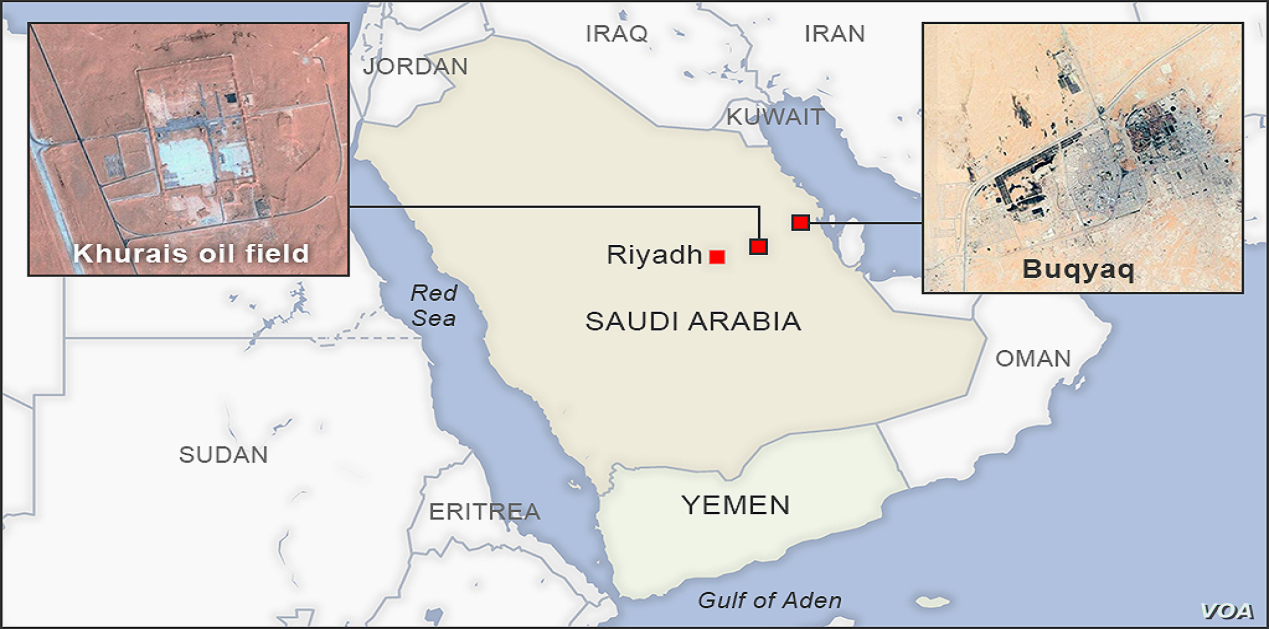
A recent attack against Saudi Aramco damaged the world’s largest oil producer and delayed oil production, roiling oil and gas markets. The Saudi government and U.S. intelligence officials have claimed the incident is the work of Iran, while Iran blamed Yemeni rebels.
This is a real-world continuation of a long-simmering cyberwar between the two countries, which has spilled over into other global powers.
In recent years, Iran has deployed destructive computer viruses against Saudi Arabia. The Kingdom and oil and gas industry have been slow to shore up their defenses, raising red flags about the possibility of longer term fal-out in the region, experts said. Investors should expect long-term cyber espionage and flare-ups of malicious activity, including the potential for destructive attacks that hurt companies in the region beyond Aramco.
Saudi Aramco declined to comment for this article.
Learning from history
Iran and Saudi Arabia have been cyberwarfare proving grounds for more than a decade.
Activity across the Gulf has concentrated on oil and gas companies, which gather terabytes of data related to drilling and oilfields. The oil and gas sector has long relied on potentially vulnerable “internet of things” devices to measure information about the availability of oil, and to power the complex machinery that finds, extracts and refines it.
Iran’s nuclear facilities were attacked by a virus called Stuxnet in the mid-2000s. This malicious software was sophisticated, built in a “modular” format. Attackers could use it not only to extract intelligence but also to control and destroy sensitive machinery.
Iran reacted to Stuxnet in a surprising way: they didn’t talk about it much at all. But they did take action, said Lieutenant Colonel Scott Applegate, an expert in the history of cybersecurity and a cyber professor at Georgetown University.
One theory is that Iran took some of what they learned from Stuxnet and created a new weapon, which they then deployed against Saudi Aramco in 2012.
That virus, known as “Shamoon,” was modular and multi-faceted like Stuxnet, but had only one purpose: To find and destroy data. It did this quite successfully, said Brian Hussey, vice president of cyber threat detection and response for cybersecurity company Trustwave.
The attack laid out Iran’s cyber capabilities for the world to see, but had little financial impact on Saudi Aramco, costing only a small fraction of the oil giant’s daily revenue, Applegate said.
“While they made a big impact on the world stage, they did not bleed over into the wider system. Historically, cyberattacks have not played a huge role in the oil and gas industry, other than from a hyperbolic rhetoric point of view,” Applegate said.
But what happened after Shamoon is more alarming.
A slow change problem
Following the Shamoon attack, Aramco took several years fortify its defenses. Saudi Arabian officials were interested in installing American-style cybersecurity best practices throughout the company.
But one cybersecurity engineer who participated in the response to Shamoon said he observed a corporate culture throughout Saudi Aramco that was resistant to change. It was difficult to “spark urgency” in workers and leaders, he said, because their jobs “simply weren’t on the line, like they are everywhere else when there’s a breach.”
Workers, many of whom were guaranteed lucrative jobs because of their family ties or tenure, expressed indifference at some security basics, he said. The result was a “slow change problem,” that made it difficult to implement the types of controls that are often required at American companies, especially following a security incident, he said.
Two other cybersecurity experts who worked in Saudi Arabia at the time concurred with these observations. All requested anonymity because they were not authorized to speak with press.
The engineer said he was not surprised when he saw that Saudia Arabia had suffered another series of attacks by the same Shamoon virus in 2017, five years after the initial attacks.
Also in 2017, reports surfaced that Saudi Aramco’s industrial safety systems may have been “tested” by hackers looking to see how they could turn those systems off. This dark turn showed how cyber conflict could have a significant effect on public safety and the wider oil and gas industry.
“There is certainly potential if they can get into the SCADA systems that there is a potential to disrupt oil and gas production, and that would be a much more serious incident,” Applegate said. He also cauthioned that Saudi Arabia’s slowness to respond tot to very similar attacks, years apart, may have been a bad sign in terms of preparedentwo
What happens next
There hasn’t been a discernible increase in cyberattack activity in the region yet, said Nicholas Hayden, global head of threat intelligence for cyber intelligence company Anomali.
But while “nothing is standing out right now in the region, there’s a good chance that there are nation-state actors” readying for potential cyber conflict, said Hayden, who has served as a cybersecurity operator in the electrical sector.
“We’re certainly paying more attention than we normally would to that area. When stuff like this happens, we tend to put our ear a little bit closer to the ground.”
Iran has been well-known for increasing cyberattacks when it comes into conflict with countries, Hayden said, and that can also mean collateral damage in other companies -- not just Saudi-owned -- doing business in the region.
Hayden said he was pessimistic about readiness in the oil and gas industry. “They’re probably not very ready. The biggest attack that they may have seen is a ransomware attack,” he said. That means oil and gas firms and their third parties may have little hands-on experience fighting a fiercer attack from a foreign adversary.
John Hultquist, director of intelligence analysis for cybersecurity company FireEye, was somewhat more optimistic. These companies have “made a lot of big strides over the years,” and have become very familiar with the threats they face from nation-states.
Still, collateral damage is often a side-effect of regional cyber conflict, Hultquist said, and companies operating in Saudi Arabia and beyond should also be alert for changes.
“Anyone with operations in Saudi Arabia, or I should say, the Gulf generally, could be a target,” in the event of cyberattacks in the region. That includes those with home bases far away from the region, he said.
The U.S., too, has been traditionally targeted by Iran in times of conflict, particularly when the federal government imposes new sanctions on them, Hultquist said. If the Trump Administration issues new sanctions, watch out.
Hultquist said he didn’t see indicators of an uptick of cyber activity in the region but that “it’s generally hard to measure espionage operations.”
All of the experts polled by CNBC agreed on one conclusion -- since Stuxnet, and despite economic odds stacked against them, Iran has become one of the world’s most significant cybersecurity powers.
“They’ve never been the most technically sophisticated,” Hultquist said. “But they have made up in their brazenness, their willingness to destroy and disrupt. They have really separated themselves on this from others, as if they have nothing to lose.”