By Tenzin Dalha
Cisco Talos, a group of world-class researchers, analysts, and engineers, recently uncovered a new cyberespionage campaign delivering a malicious Microsoft PowerPoint document using a mailing list run by the Central Tibetan Administration (CTA). The document is a copy of a legitimate PDF file titled “Tibet was never a part of China,” which is available for download from the CTA’s website tibet.net. The malicious version, however, contains a Remote Access Trojan (RAT). The email is targeted at pro-Tibet groups and individuals in order to distribute what has been dubbed ExileRAT. The attack delivers an Android- and Window-based Trojan capable of stealing system and personal information, terminating or launching process, or carrying out surveillance and the theft of data.
As the volume and sophistication of cyberattacks grow worldwide, it is essential for the CTA and Tibetan nongovernmental organizations (NGOs) to take necessary precautions to protect their sensitive data and personal information of employees.
The Tibetan community has been persistently targeted by digital espionage operations for over a decade. The scale of China’s operation was not clear until 2009, when the University of Toronto’s Citizen Lab released a report titled “Tracking Ghostnet.” The report explicitly laid out, for the first time, the scope of cyberespionage and how deeply it had infiltrated the Tibetan movement, including the office of the Dalai Lama.
The recent cyberespionage attempt targeting the CTA and Tibetan NGOs is just one facet of more comprehensive and sophisticated cyberattacks perpetrated by Chinese state-sponsored hackers. The goal is primarily to gain entry into the network system of the CTA, and consequently to monitor activities and extract information using various social engineering techniques.
Last year, Citizen Lab documented the use of suspicious emails with links to complex malware in its January 30, 2018 report, “Spying on a Budget: Inside a Phishing Operation With Targets Inside the Tibetan Community.” The source of the phishing operation could not be determined, according to Citizen Lab; Tibetans are inclined to believe that the Chinese government is behind these malicious activities. As Citizen Lab notes, “Uyghurs, Falun Gong supporters, and Tibetan groups are well documented targets of digital espionage operations that are often suspected to be carried out by operators directly sponsored or tacitly supported by Chinese government agents.”
The Tibetan Computer Resource Center (TCRC) comes under the direct administration of the Department of Information and International Relations under the CTA. Speaking to the author, Mr. Tenzin Lekshey, director of the TCRC, said: “In the past six months, we have been observing an increase in phishing operations targeting the Tibetan community. We created awareness amongst users about phishing attacks in a variety of ways, including educating [about] basic and safe browsing practices and also by notifying users of dangerous links in email and browsers [and] preventing suspicious account sign-ins and conducting workshops. We have suggested not to open unsolicited attachments from suspicious email accounts.”
 He further emphasized that “earlier, cyberattacks on Tibetan organizations were restricted only to special occasions, like the anniversaries of March 10th Tibetan uprising day and the Dalai Lama’s birthday etc… but now the trend has completely changed. Tibetan organizations in Dharamshala are targeted with Distributed Denial of Service and phishing attacks frequently.”
He further emphasized that “earlier, cyberattacks on Tibetan organizations were restricted only to special occasions, like the anniversaries of March 10th Tibetan uprising day and the Dalai Lama’s birthday etc… but now the trend has completely changed. Tibetan organizations in Dharamshala are targeted with Distributed Denial of Service and phishing attacks frequently.”
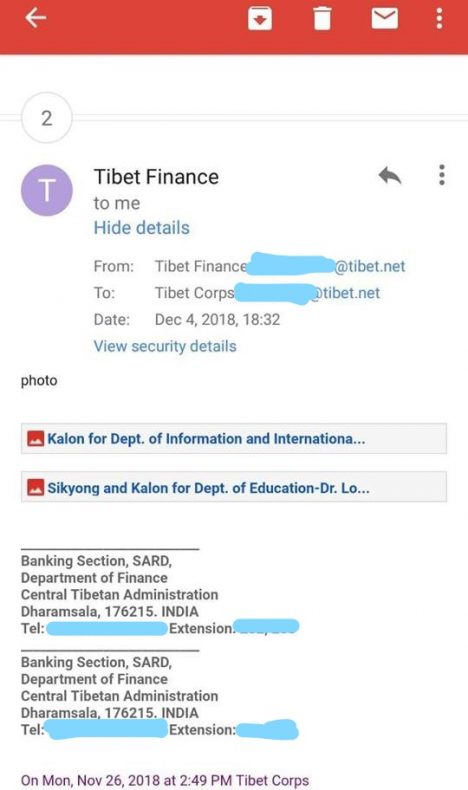
Figure 1: Most spear-phishing files come in .zip format. Hackers usually dress .zip files as other files in disguise, as in the below screenshot showing a malicious email sent ito Tibet Corps in December 2018.
Spear-Phishing Attacks
Attackers focus primarily on gaining access to Google accounts and more recently into the personal WhatsApp accounts of CTA staff. They have been targeting researchers of the Tibet Policy Institute and staff of the CTA’s Department of Religion and Culture. In an interview with the author, malware analysis expert Tenzin Chokden of the TCRC said: “Scammers are tricking staff of CTA into clicking on fake links that are identical to original attachments, and then [the attackers] steal people’s information and data. Staff are targeted via email and Google drive to their Gmail account. The emails often include an attachment or file, resembling a standard email. Many receivers mistakenly presume it to be from their trusted friends or colleagues.
“While it looks like a standard PDF file with Adobe icon, when clicked, this opens a new tab with a page which closely resembles the real Gmail login page, and asks the user to log in again. However, the page is actually a portal for hackers to steal targeted email addresses and passwords, and get full access to the user’s account.” And even worse, if the user uses the same login details for other websites or accounts, the hackers will be able to gain access to these details.
He further adds, “it is important to know your online digital footprint and take necessary steps to safeguard your data.”
This example clearly indicates that one of the email account’s details are already compromised. The file names are broadly categorized under different set themes, including project-related, the budget, and diplomatic issues, largely determined by the types of organizations the hackers are targeting.
This type of attack is known as spear-phishing: sending common emails from identical addresses to many email addresses, hoping that just some of the malware recipients will click on a malicious link (even if by accident) or download an infected file. It pays off for the hackers: the infection rate can be as high as 50 percent.
The cyberespionage campaign is evolving tactics but the operations keep the CTA and its staff as their prime target. The attackers rely more and more on spear–phishing instead of malware and other attacks.
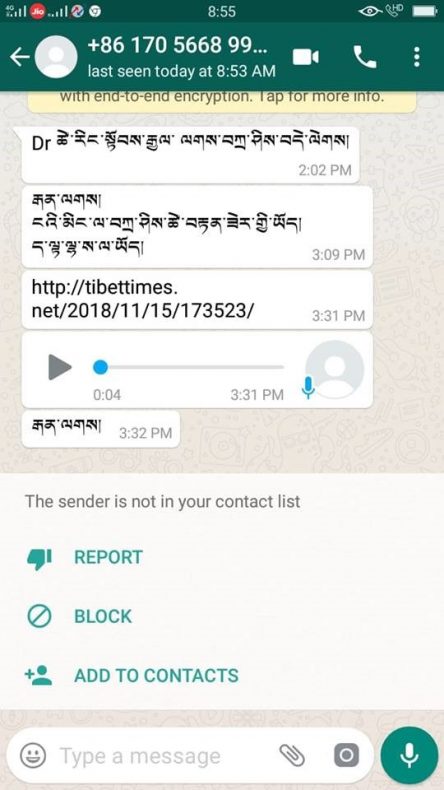
Figure 2: A WhatsApp message sent from Tibet to a staff member of the Department of Religion and Culture on December 5. The number is registered in Lhasa.
Tibetan cyber expert and director of Digital Security Program at the Tibet Action Institute, Lobsang Gyatso Sither, explains that the new targeting of WhatsApp accounts is even more dangerous. “A WhatsApp attack will be worse, since it is basically a personal attack. Unknowingly, if an individual clicks the suspicious links, it will compromise the personal details and contact inside the phone. The hackers can then further spread links and virus to other contacts. Thus, it is important not to click on such links to prevent further attacks.”
These attacks are often designed to target a large number of victims at once. Any such occurrences should immediately be reported to experts; it’s unlikely only a single person would receive such a message. The safest approach is to keep away from unidentified numbers and email IDs, who sends links anonymously.
Samdup Choephel, an independent cybersecurity researcher based in Dharamshala who is involved in helping Tibetan NGOs fix hacked websites, said, “I am overwhelmed to see the increased number of Tibetans becoming aware of the risks in clicking on unidentified ‘attachments’ and knowing the risks of creating weak passwords. Still many people are reluctant to update their password to enable the two-factor authentication. Such a small step will give a hard time to anybody who tries to get your credentials. A strong password provides essential protection; commonly used passwords enable intruders to easily gain access and control of a computing devise.”
The TCRC observes that of the cyberattacks on the CTA during the last many years, more than 90 percent are spear-phishing attacks. This is primarily aimed to steal the project ideas and schedules according to Tenzin Lekshey. But some hackers are increasingly using sophisticated techniques. They adopt new techniques to conceal their activities. Due to the frequent attacks and complicated interchannel relations within Chinese cyberspace, it is really hard to prevent cyberattacks completely.
Conclusion and Recommendations
It’s very difficult to put technical controls into place to prevent humans from making mistakes. To stymie these attacks, email users have to do the right things by following safe and secure practices. Updated software is needed for PC and mobile applications.
To minimize the number of cyberattacks, Tibetan computer users should be aware of the risks involved in opening unsolicited attachments and suspicious links through email. Similar messages are used to steal people’s personal information. Unless you trust the sender, don’t click links or reply with personal information.
The hackers are having a two-fold impact. Beside deliberately exploiting Tibetan computer systems — including installing surreptitious monitoring program on computers and creating fake IDs – they more indirectly weaken the harmony of the community by disrupting the ability of Tibetan exiles to exchange information and communicate through the internet. Tibetan communities should be aware that the systems are built to certain security standards, they should be properly trained to prevent cyberattacks that target the disclosure of important files.
Tibetans both as individuals and as a community are being targeted with some of the most sophisticated malware attacks and cybersurveillance by the Chinese government. As long as Tibetans equip themselves with the knowledge and skills to defend against such attacks and understand the threats involved, technology can be one of most powerful tools in the struggle for freedom.
Tenzin Dalha is a research fellow at the Tibet Policy Institute, doing research on Chinese cybersecurity policy and the social media landscape of Tibetan society.

No comments:
Post a Comment