By Sergiu Gatlan
 A new year in review report from Symantec shows that formjacking accompanied by supply chain attacks were the fastest growing threats of 2018, while living-off-the-land (LotL) attacks saw a large boost in adoption from threat actors, with PowerShell scripts usage, for example, seeing a formidable 1000% increase.
A new year in review report from Symantec shows that formjacking accompanied by supply chain attacks were the fastest growing threats of 2018, while living-off-the-land (LotL) attacks saw a large boost in adoption from threat actors, with PowerShell scripts usage, for example, seeing a formidable 1000% increase.
Symantec's 2019 Internet Security Threat Report also shows that cryptojacking attacks have increased in number four times but went into a downward spiral with the decreasing value of cryptocurrency, encouraging threat actors to switch to other ways of profiting from compromised targets.
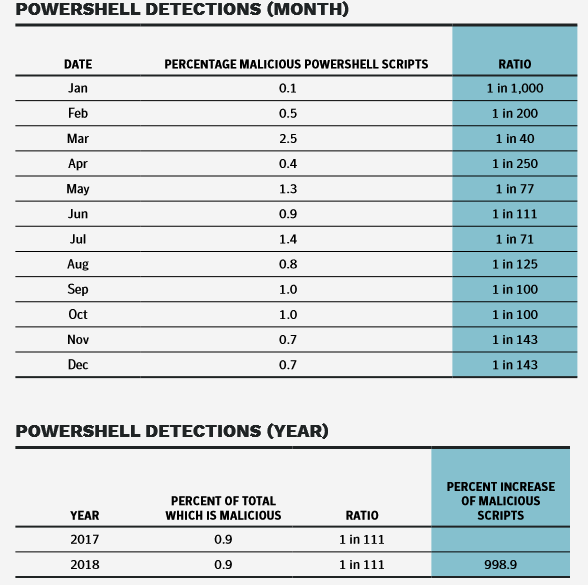
Cryptojacking occurred 4x more than 2017, but trended down at the end of the year coinciding with cryptocurrency values tanking. Other high level stats include 78% increase in supply chain attacks, 100% increase in malicious powershell scripts and almost half of all malicious email attachments are Office files.
Formjacking top threat during 2018
Threat actors were able to compromise 4,800+ websites every month during 2018, using injected JavaScript code to steal payment information such as debit and credit cards from customers of eCommerce sites.
The most high-profile formjacking attacks were against British Airways and Ticketmaster, but according to Symantec cyber criminals who used this technique also got a huge chunk of their illicit earnings from smaller online retailers who accept payments from their customers via online portals.
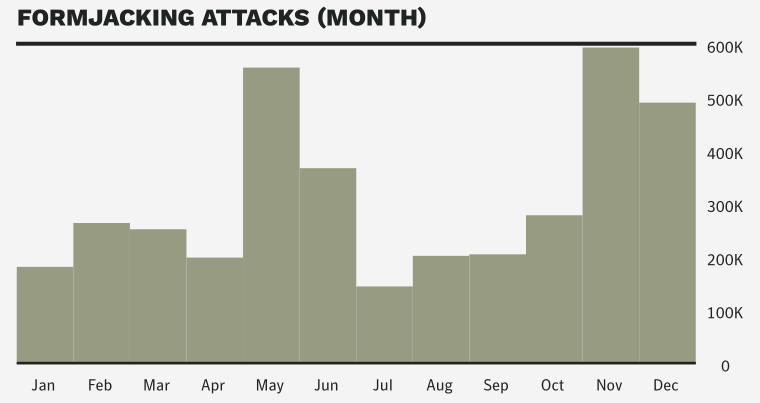
Symantec blocked more than 3.7 million formjacking attempts in 2018, with more than 1 million of those blocks occurring in the last two months of the year alone. Formjacking activity occurred throughout 2018, with an anomalous spike in activity in May (556,000 attempts in that month alone), followed by a general upward trend in activity in the latter half of the year.
The growth in the number of formjacking attacks during 2018 can also be explained by the ever decreasing value of cryptocurrencies which convinced the hackers who previously used compromised websites for cryptojacking to switch to stealing credit cards for higher profit margins of tens of millions of dollars throughout 2018.
As detailed by Symantec in the report, given that each stolen card can be sold on underground markets for up to $45, if the hackers would be able to steal roughly 10 cards for each website they manage to compromise, they would be able to walk away with roughly $2.2 million per month.
Supply chain and LotL attacks also on the rise
During 2018, the number of supply chain attacks was also on an increasing course having inflated by approximately 78%. Also, living-off-the-Land (LotL) attacks were one of the most important tools in the arsenal of bad actors, allowing them to stay unnoticed while conducting complex attacks.
The use of malicious PowerShell scripts for example expanded by a remarkable 1,000%, following the overall trend of miscreants moving to LotL techniques to avoid being detected for as much time as possible.
A highly common attack scenario would see malicious actors using Microsoft Office documents containing specially crafted macros designed to run PowerShell scripts which would download and launch malicious payloads on the victim's computer.
Office files on their own were more and more present during malware campaigns, with malicious emails switching from delivering malware to targets using URLs to Office files containing macro downloaders. To be more exact, malicious Office documents accounted for "48 percent of malicious email attachments, jumping from 5 percent in 2017."
Symantec blocks 115,000 malicious PowerShell scripts each month, but this number accounts for less than one percent of overall PowerShell usage. A sledgehammer approach toward blocking all PowerShell activity would disrupt business, further illustrating why LotL techniques have become the preferred tactic for many targeted attack groups, allowing them to fly under the radar.
Cryptojacking and ransomware on a downward spiral
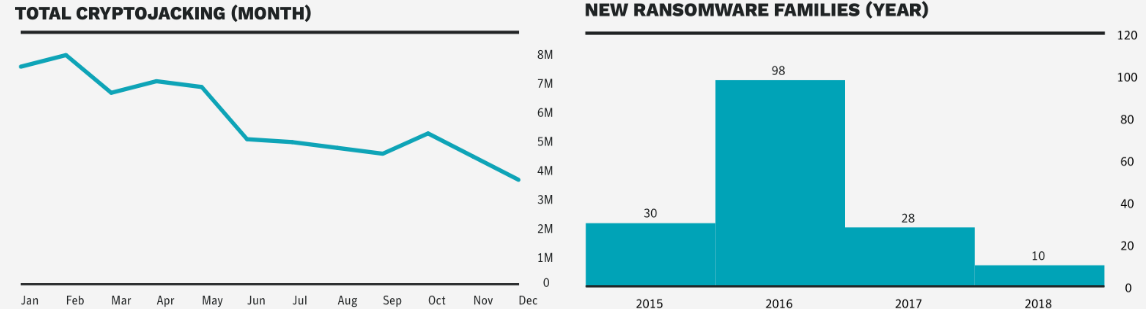
While previously the go-to malware family, cryptojacking saw a quick decline during the second half of 2018 following the devaluation of all cryptocurrencies during the same period of time. Symantec "blocked 69 million cryptojacking events—four times as many events as we blocked in 2017. However, cryptojacking activity declined by 52 percent between January and December 2018."
Ransomware infections also fell, seeing an year-over-year decrease of approximately 20%, although enterprises were also actively targeted and experiencing 12% more attacks when compared to 2017. In addition, according to Symantec's report, fewer new ransomware families have been detected in 2018, a clear sign that threat actors will rely on ransomware a lot less in the future to monetize their skills.
Mobile ransomware however thrived, with the number of infection boosted by around 30% when compared to 2017, even though mobile malware infections as a whole saw a decrease in numbers. 63% of all mobile ransomware affected devices from U.S., while China and Germany were way behind with 13% and 10% respectively.
Symantec used its Global Intelligence Network (GIN) which includes over 123 million attack sensors to gather data for its 2019 Internet Security Threat Report, allowing it to analyze roughly 9 petabytes of information recorded at a speed of a few thousand threat events per second.
Symantec's GIN is designed to keep a close eye on threat activities impacting more than 300,000 organizations and businesses around the world which use its security solutions to protect endpoints and networks.
No comments:
Post a Comment