By SYDNEY J. FREEDBERG JR.
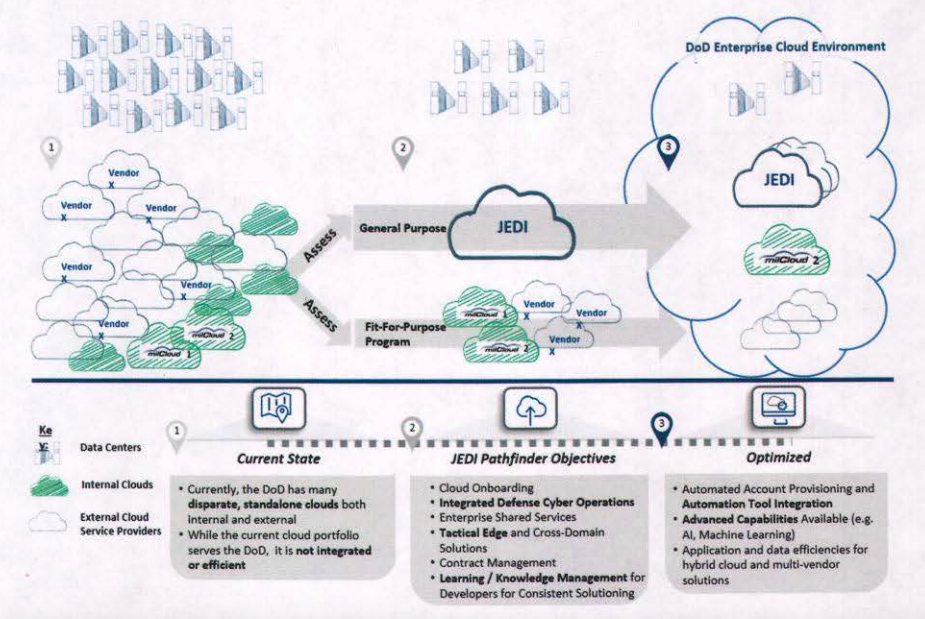
The Defense Department’s strategy to transition to cloud computing. Note the prominent role for the JEDI project.
ARMY-NAVY COUNTRY CLUB, ARLINGTON: In just three weeks, the Army will roll out a new policy for cloud computing, officials said this afternoon. The strategy will open up new options for outsourcing functions to contractors that the government currently does for itself.
“The rollout comes next month,” said Col. Jeth Rey, Army Cyber Command’s director of operations, at an AFCEA luncheon here. “This is very new to us and we want to explore it.”
“Currently, how we operate is government-owned, government-operated equipment; we’re exploring the possibility of contractor-owned, contractor operated, [but] government owns the sites,” Rey continued. “That’s the lesson learned from the Navy and the Air Force.”
“Next month, CIO/G6” – the Army’s Chief Information Officer, Lt. Gen. Bruce Crawford – “will hold his annual conference [aka AFCEA’s annual Army Signal Conference, March 12th-15th]. I recommend each and everyone one of you to come out,” Rey told the audience, mostly contractors. “We will talk ‘as a service’ at that event.”
“As a service” is an IT sector term of art for the practice, increasingly popular in the private sector, of outsourcing key network functions. “Infrastructure as a Service” (IaaS), for example, means effectively renting servers from a cloud computing company, rather than buying, owning, and operating your own. “Software as a Service” (SaaS) goes farther: You not only rent the hardware, you rent the software you run it on as well, with the service provider doing all the downloading, uploading, and installation for you. Wikipedia’s page on “As A Service” currently lists some 38 variations, from “artificial intelligence” (AIaaS) to “everything” (XaaS).
Col. Rey – soon to be promoted to one-star-general – confirmed to me and another reporter after the event that a wide range of such options will be included: “We’ll do the roll-out in March,” he said, “[for] everything as a service.”
Rey and the other three Army colonels at today’s AFCEA event were shy about details, understandably unenthusiastic about stealing any thunder from their superiors. Besides Crawford, the three-star CIO, scheduled speakers at next month’s conference include the one-star director of the Army AI Task Force (Brig. Gen. Matthew Easley); the two-stars running the Army network modernization taskforce, Maj. Peter Gallagher, and the network acquisitions program, PEO-C3T’s Maj. Gen. David Bassett; and the four-star vice-chief of Army staff, Gen. James McConville.
What Rey & co. would divulge today, however, is that the Army is looing to do a number of as-a-service pilots, both internally – the leading one will be at the newly created Army Futures Command, whose Austin HQ has no existing Army infrastructure to fall in on – and externally with the Air Force and Navy.
The biggest obstacles are cultural, said Col. Carl Young, who heads the architecture and data division of CIO Crawford’s Pentagon staff. “It’s the various subcultures of, ‘well, this is my data, and not our data, [and] I don’t want you using it.’”
But, Young went on, “those walls are beginning to erode and break down, and we are sharing across the wide array of Army elements and joint elements… partnering with the Air Force and the Navy right now to learn how they do it.”
The Army needs to find partners, both in the military and the private sector, because it simply can’t do everything that needs doing in-house, Young said. IT has become so sprawling, feudal, and fragmented that “we don’t have an authoritative card catalogue” of every system out there, let alone what it all does, he said.
“We’ve got to get that into one matrix where we can see comprehensively, what are our risk factors, what are our implementation, goals, what can we afford not to pay for?” Young said. “Because we cannot to do it all. It’s already a $12.5 billion enterprise [and] that’s not enough to do what we all want it to do.”
“Maybe the [Army] network doesn’t need to perform a particular function, maybe it needs to be outsourced – that’s one of the things Army cyber is looking at that,” Young said, with a nod to Rey’s organization. “Maybe it doesn’t need to provide the function at all.”
But aren’t some military functions too important to outsource – “inherently governmental” to use the term of art – because they are matters of national policy, life, and death? Isn’t the network a weapon?
“That’s a concern,” Rey said, “but when we look at our network as a weapon system, [the end user device,] the end point, is always going to be in the hands of some government employee. [The commercial sector,] we’re just asking them for transport “ – that is, of the data from one government user to another. “We’ve been using commercial transport for years now, so it’s nothing new.”



No comments:
Post a Comment