Outer space exploration has turned into a key part of a modern society’s functionality with several services including weather, communication, Internet, banking and navigation, supported by satellites orbiting the Earth. India being one of the major actors in outer space has in many ways led the usage of satellites for the benefit of the society. With the space infrastructure of India powering the economy, is there a case for exploring the defence of these vital systems? Moreover, given that the geopolitics and security scenarios are changing with respect to the utilisation of outer space, should India explore its capabilities and capacities built in the country for the past 50 years for dedicated space defence operations? The present work provides insights on the key question as to are we or are we not at a tipping point where the government needs to draw a vision in securing national interests via creation of a Defence Space Agency as an interim arrangement until a full-fledged Aerospace Command is in place. If so, what are its technological, organisational and policy facets?
Outer space exploration has turned into a key part of a modern society’s functionality with several services including weather, communication, Internet, banking and navigation, supported by satellites orbiting the Earth. India being one of the major actors in outer space has in many ways led the usage of satellites for the benefit of the society. With the space infrastructure of India powering the economy, is there a case for exploring the defence of these vital systems? Moreover, given that the geopolitics and security scenarios are changing with respect to the utilisation of outer space, should India explore its capabilities and capacities built in the country for the past 50 years for dedicated space defence operations? The present work provides insights on the key question as to are we or are we not at a tipping point where the government needs to draw a vision in securing national interests via creation of a Defence Space Agency as an interim arrangement until a full-fledged Aerospace Command is in place. If so, what are its technological, organisational and policy facets?18 June 2018
Creation of a defence space agency: A new chapter in exploring India’s space security
 Outer space exploration has turned into a key part of a modern society’s functionality with several services including weather, communication, Internet, banking and navigation, supported by satellites orbiting the Earth. India being one of the major actors in outer space has in many ways led the usage of satellites for the benefit of the society. With the space infrastructure of India powering the economy, is there a case for exploring the defence of these vital systems? Moreover, given that the geopolitics and security scenarios are changing with respect to the utilisation of outer space, should India explore its capabilities and capacities built in the country for the past 50 years for dedicated space defence operations? The present work provides insights on the key question as to are we or are we not at a tipping point where the government needs to draw a vision in securing national interests via creation of a Defence Space Agency as an interim arrangement until a full-fledged Aerospace Command is in place. If so, what are its technological, organisational and policy facets?
Outer space exploration has turned into a key part of a modern society’s functionality with several services including weather, communication, Internet, banking and navigation, supported by satellites orbiting the Earth. India being one of the major actors in outer space has in many ways led the usage of satellites for the benefit of the society. With the space infrastructure of India powering the economy, is there a case for exploring the defence of these vital systems? Moreover, given that the geopolitics and security scenarios are changing with respect to the utilisation of outer space, should India explore its capabilities and capacities built in the country for the past 50 years for dedicated space defence operations? The present work provides insights on the key question as to are we or are we not at a tipping point where the government needs to draw a vision in securing national interests via creation of a Defence Space Agency as an interim arrangement until a full-fledged Aerospace Command is in place. If so, what are its technological, organisational and policy facets?How Using Algorithms Can Worsen Inequality
India’s Strategic Expansion in the Pacific Islands
By Balaji Chandramohan
 As India’s politico-military orientation is adjusting to the change in the United States’ Command structure and geostrategic orientation from the Asia-Pacific to Indo-Pacific, the region of Pacific Islands will get more strategic attention from India. To start with, India’s maritime strategic orientation is toward the rimlands of Eurasia, which is reflected in it giving greater strategic importance to the littoral areas in the greater Indo-Pacific region (such as the Bay of Bengal, Arabian Sea, and South China Sea). Therefore, the region of the Pacific Islands in Oceania had long been neglected in India’s maritime strategic thinking.
As India’s politico-military orientation is adjusting to the change in the United States’ Command structure and geostrategic orientation from the Asia-Pacific to Indo-Pacific, the region of Pacific Islands will get more strategic attention from India. To start with, India’s maritime strategic orientation is toward the rimlands of Eurasia, which is reflected in it giving greater strategic importance to the littoral areas in the greater Indo-Pacific region (such as the Bay of Bengal, Arabian Sea, and South China Sea). Therefore, the region of the Pacific Islands in Oceania had long been neglected in India’s maritime strategic thinking.What’s Next for the India-Russia Strategic Partnership?
By Rajeswari Pillai Rajagopalan
 When Indian Prime Minister Narendra Modi and Russian President Vladimir Putin had an “informal” meeting in Sochi in late May, the two leaders discussed a number of bilateral issues such as military and defense cooperation and international issues relevant to both India and Russia. The meeting once again put the attention on the strategic partnership between New Delhi and Moscow, which continues to be significant, but also faces a number of challenges.
When Indian Prime Minister Narendra Modi and Russian President Vladimir Putin had an “informal” meeting in Sochi in late May, the two leaders discussed a number of bilateral issues such as military and defense cooperation and international issues relevant to both India and Russia. The meeting once again put the attention on the strategic partnership between New Delhi and Moscow, which continues to be significant, but also faces a number of challenges.Islamic State Emboldened in Afghanistan
By: Farhan Zahid
From its establishment in September 2014, Islamic State’s arm in Afghanistan, its Khorasan province entity (IS-K), found itself the target of attacks by Afghan Taliban forces and strikes by the U.S. military in conjunction with the Afghan security forces. The group weathered significant losses and entrenched itself in the districts of eastern Afghanistan. In recent months, however, an improvement in relations with the Taliban has allowed it to focus on carrying out a series of bloody attacks.
Beginnings
How the US Is Indirectly Arming the Taliban
By Austin Bodetti
 While empowering allied militaries to confront insurgents on their own has become the cornerstone of the American approach to counterterrorism, that strategy comes with a drawback: those militaries often lose Western-supplied equipment to American-labeled terrorist organizations. In 2014, the Islamic State captured weapons from Syrian rebels armed by the United States. In 2015, the Iranian-backed Iraqi militia Kataib Hezbollah acquired several M1 Abrams tanks sold to the Iraqi Security Forces by the U.S. This problem has spread as far as Afghanistan, where much of the Taliban’s armory comes from American equipment given to the Afghan military and police.
While empowering allied militaries to confront insurgents on their own has become the cornerstone of the American approach to counterterrorism, that strategy comes with a drawback: those militaries often lose Western-supplied equipment to American-labeled terrorist organizations. In 2014, the Islamic State captured weapons from Syrian rebels armed by the United States. In 2015, the Iranian-backed Iraqi militia Kataib Hezbollah acquired several M1 Abrams tanks sold to the Iraqi Security Forces by the U.S. This problem has spread as far as Afghanistan, where much of the Taliban’s armory comes from American equipment given to the Afghan military and police.China-US Confrontation: Russian Perspective
4 things to watch as Trump's tariffs hit China
The Trump administration is moving ahead with a plan to assess steep new tariffson $50 billion worth of products made in China and exported to the U.S. The United States Trade Representative on Friday released a list of $34 billion in Chinese goods that would face tariffs of 25 percent. President Donald Trump approved the tariffs after a meeting with trade and Cabinet officials on Thursday. The USTR said it would initially impose tariffs on 818 products made in China, effective July 6. An additional 284 Chinese imports, worth $16 billion, also could face tariffs pending a final decision by the trade office and time to solicit public comment. "We must take strong defensive actions to protect America's leadership in technology and innovation against the unprecedented threat posed by China's theft of our intellectual property, the forced transfer of American technology and its cyber attacks on our computer networks," said U.S. Trade Representative Robert Lighthizer said in a statement.
Who lost the South China Sea?
 US Defense Secretary Jim Mattis has spoken out against China’s strategy of ‘intimidation and coercion’ in the South China Sea, including the deployment of anti-ship missiles, surface-to-air missiles and electronic jammers, and, more recently, the landing of nuclear-capable bomber aircraft at Woody Island. There are, Mattis warned, ‘consequences to China ignoring the international community’. But what consequences? Two successive US administrations—Barack Obama’s and now Donald Trump’s—have failed to push back credibly against China’s expansionism in the South China Sea, which has accelerated despite a 2016 international arbitral tribunal ruling invalidating its territorial claims there. Instead, the US has relied on rhetoric or symbolic actions.
US Defense Secretary Jim Mattis has spoken out against China’s strategy of ‘intimidation and coercion’ in the South China Sea, including the deployment of anti-ship missiles, surface-to-air missiles and electronic jammers, and, more recently, the landing of nuclear-capable bomber aircraft at Woody Island. There are, Mattis warned, ‘consequences to China ignoring the international community’. But what consequences? Two successive US administrations—Barack Obama’s and now Donald Trump’s—have failed to push back credibly against China’s expansionism in the South China Sea, which has accelerated despite a 2016 international arbitral tribunal ruling invalidating its territorial claims there. Instead, the US has relied on rhetoric or symbolic actions.In China’s Far West, Companies Cash in on Surveillance Program That Targets Muslims
BY CHARLES ROLLET
In the far western region of Xinjiang, China has created one of the world’s most sophisticated and intrusive state surveillance systems to target the predominantly Muslim Uighur ethnic minority. Part of what Beijing calls its anti-terrorism campaign, the system includes mandatory facial-recognition scans at gas stations and Wi-Fi sniffers that secretly collect data from network devices. Over the past two years, the technology has helped authorities round up an estimated hundreds of thousands of Uighurs and other Muslims and lock them up in clandestine camps that China calls “re-education centers.”
Trump’s next target: NATO
By PAUL TAYLOR
 After watching the G7 train wreck aghast, senior officials at NATO headquarters are quaking in their boots at the prospect of hosting a summit of the Western defense alliance featuring a raging Donald Trump in Brussels. Far from showcasing transatlantic unity and resolve, they fear the 24-hour gathering of leaders of the 29-nation alliance, scheduled for about a month from now, could turn into round 2 of the rumble in Quebec, with the U.S. president on the rampage against the Europeans and Canadians over their allegedly unfair trade surpluses and puny military spending, leaving NATO in tatters. It is entirely legitimate for the United States to press NATO nations to pay more toward their own defense. But America needs like-minded friends and allies, and Trump cannot afford to go on treating them as rivals or threats to its security.
After watching the G7 train wreck aghast, senior officials at NATO headquarters are quaking in their boots at the prospect of hosting a summit of the Western defense alliance featuring a raging Donald Trump in Brussels. Far from showcasing transatlantic unity and resolve, they fear the 24-hour gathering of leaders of the 29-nation alliance, scheduled for about a month from now, could turn into round 2 of the rumble in Quebec, with the U.S. president on the rampage against the Europeans and Canadians over their allegedly unfair trade surpluses and puny military spending, leaving NATO in tatters. It is entirely legitimate for the United States to press NATO nations to pay more toward their own defense. But America needs like-minded friends and allies, and Trump cannot afford to go on treating them as rivals or threats to its security.Trump's big deal
Raj Chengappa
 It was without doubt histrionics of the grandest scale. Donald Trump looked smug as he made history by shaking hands with Kim Jong-un on June 12 at a Singapore luxury resort. In doing so, he became the first American president to hold a summit meeting with a North Korean head of state. The two leaders were a study in contrast, Trump at 72 with his wavy blond hair and Kim a portly 34 with his dark hip-hop bouffant. One was the leader of the free world, the other an epitome of the unfree one. But they had much in common too. Apart from their affluent upbringing, both have displayed their megalomaniacal impulses as rulers of their respective countries. To be fair to Trump, he is only a bully and has never indulged in the kind of brutal repression that the young North Korean supremo unleashed in his country. With their fierce rhetoric, both leaders had brought the world the closest it has been to a nuclear Armageddon since the perilous Cold War years.
It was without doubt histrionics of the grandest scale. Donald Trump looked smug as he made history by shaking hands with Kim Jong-un on June 12 at a Singapore luxury resort. In doing so, he became the first American president to hold a summit meeting with a North Korean head of state. The two leaders were a study in contrast, Trump at 72 with his wavy blond hair and Kim a portly 34 with his dark hip-hop bouffant. One was the leader of the free world, the other an epitome of the unfree one. But they had much in common too. Apart from their affluent upbringing, both have displayed their megalomaniacal impulses as rulers of their respective countries. To be fair to Trump, he is only a bully and has never indulged in the kind of brutal repression that the young North Korean supremo unleashed in his country. With their fierce rhetoric, both leaders had brought the world the closest it has been to a nuclear Armageddon since the perilous Cold War years.Trump must still hold North Korea accountable for cyberattacks
Canadian Foreign Minister Sharply Rebukes Trump’s Trade Policy and Worldview
 Canadian Foreign Minister Chrystia Freeland, in Washington on Wednesday, promised a “dollar-for-dollar response” to President Donald Trump’s trade tariffs and said American businesses and consumers would pay a price for their country’s protectionism. Her comments, coming just a week after a divisive meeting of the leading industrialized democracies known as the G-7, marked one the sharpest Canadian rebukes of the United States in recent memory. Freeland described Trump’s plan to slap tariffs on Canada under the pretext of national security as ridiculous and urged the United States to invest in its international alliances.
Canadian Foreign Minister Chrystia Freeland, in Washington on Wednesday, promised a “dollar-for-dollar response” to President Donald Trump’s trade tariffs and said American businesses and consumers would pay a price for their country’s protectionism. Her comments, coming just a week after a divisive meeting of the leading industrialized democracies known as the G-7, marked one the sharpest Canadian rebukes of the United States in recent memory. Freeland described Trump’s plan to slap tariffs on Canada under the pretext of national security as ridiculous and urged the United States to invest in its international alliances.How Russia-Israel engagement is benefiting Iran
Hamidreza Azizi
 On June 9, Iranian President Hassan Rouhani met with Russian President Vladimir Putin on the sidelines of the Shanghai Cooperation Organization’s annual summit in the Chinese city of Qingdao. Among the issues discussed in the meeting, the two sides touched upon their regional cooperation, especially in Syria, calling it effective in preserving regional stability. According to Rouhani, “The cooperation between Iran and Russia in the war against Daesh [the Islamic State] … has been effective, and such cooperation will continue.” For his part, Putin stressed that the cooperation between Iran and Russia “will go on, as for the settlement of the crisis in Syria.”
On June 9, Iranian President Hassan Rouhani met with Russian President Vladimir Putin on the sidelines of the Shanghai Cooperation Organization’s annual summit in the Chinese city of Qingdao. Among the issues discussed in the meeting, the two sides touched upon their regional cooperation, especially in Syria, calling it effective in preserving regional stability. According to Rouhani, “The cooperation between Iran and Russia in the war against Daesh [the Islamic State] … has been effective, and such cooperation will continue.” For his part, Putin stressed that the cooperation between Iran and Russia “will go on, as for the settlement of the crisis in Syria.”The battlefield tablet that knows you have just one free hand
By: Kelsey Atherton
/arc-anglerfish-arc2-prod-mco.s3.amazonaws.com/public/C4XBGAAY4RD3JKHW5FMGUKXWYQ.jpg) The smartphone is such an integral part of modern life that it’s only natural to see battlefield adaptations. Today’s novelty comes from Swedish defense giant Saab, and goes by “Soldier sPAD,” to give the convenience and utility of a small touch-screen computer, but make sure it can actually work in the kind of situations where soldiers might find iPhones or Androids lacking. You only have two hands and you need them in combat. This fact means that a handheld unit must not only be easy to operate, but also one hand operated. Saab’s Soldier sPAD system consists of two main parts: a rugged handheld pad and a connection hub allowing individual placement, peripheral connectivity and power support. Unlike a rugged computer, the sPAD is designed to be used with only one hand and is not much bigger than an iPhone. The symmetrical topmost layout of the buttons allows for one hand operation, left or right. Its rugged design is able to sustain the shocks and harsh environments in which soldiers often operate.
The smartphone is such an integral part of modern life that it’s only natural to see battlefield adaptations. Today’s novelty comes from Swedish defense giant Saab, and goes by “Soldier sPAD,” to give the convenience and utility of a small touch-screen computer, but make sure it can actually work in the kind of situations where soldiers might find iPhones or Androids lacking. You only have two hands and you need them in combat. This fact means that a handheld unit must not only be easy to operate, but also one hand operated. Saab’s Soldier sPAD system consists of two main parts: a rugged handheld pad and a connection hub allowing individual placement, peripheral connectivity and power support. Unlike a rugged computer, the sPAD is designed to be used with only one hand and is not much bigger than an iPhone. The symmetrical topmost layout of the buttons allows for one hand operation, left or right. Its rugged design is able to sustain the shocks and harsh environments in which soldiers often operate.Bad Cybersecurity? No Access To DoD Networks
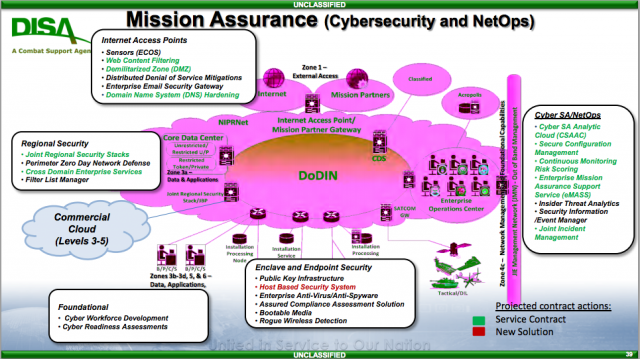
"We’re going to turn that off unless you secured that properly. Whoa! That's a very different mindset," Col. Straub told me. "The availability of the network versus the defense of the network, that's something we’re trying to get commanders to think about.".
A DISA schematic of the Department of Defense Information Networks (DoDIN).
ARMY-NAVY COUNTRY CLUB, ARLINGTON: If your unit’s network is not secure, you and your fellow warriors may lose access to the wider Defense Department network until you fix it. That’s the new philosophy — not yet a formal policy — that two Defense Information Systems Agency officials laid out to the industry group AFCEAhere, just two miles from the Pentagon.
Top Marine says cyber warriors must get more flexibility
By: Justin Lynch
/arc-anglerfish-arc2-prod-mco.s3.amazonaws.com/public/EUNXF2M6CVAOXEHZPVQJZY56X4.jpg) The Marine Corps must be “more flexible” when it comes to retaining cyber warriors, its top officer said, a recognition that the service needs to bolster its recruiting effort for the digital fight. During a June 12 speech, Marine Corps Commandant Gen. Robert Neller said that cyber fighters may follow a different career trajectory than traditional recruits. “If you get qualified as a cyber Marine, you ain’t ever leaving, unless you want to. If you want to stay there and do ones and zeros” that’s fine, Neller said. The recruitment effort laid out during the 69th Current Strategy Forum at the U.S. Naval War College in Newport, R.I. was part of a futuristic vision for the Marines that embraced digital war-fighting. The speech served as a rejection a force that will rely solely on bullets and bombs. Instead, he highlighted a Marine Corps that will also battle in ones and zeroes. He portrayed the Corps as in the middle of a digital battle, “in phase 2.5 against potential countries and adversaries,” an apparent reference to different stages of combat.
The Marine Corps must be “more flexible” when it comes to retaining cyber warriors, its top officer said, a recognition that the service needs to bolster its recruiting effort for the digital fight. During a June 12 speech, Marine Corps Commandant Gen. Robert Neller said that cyber fighters may follow a different career trajectory than traditional recruits. “If you get qualified as a cyber Marine, you ain’t ever leaving, unless you want to. If you want to stay there and do ones and zeros” that’s fine, Neller said. The recruitment effort laid out during the 69th Current Strategy Forum at the U.S. Naval War College in Newport, R.I. was part of a futuristic vision for the Marines that embraced digital war-fighting. The speech served as a rejection a force that will rely solely on bullets and bombs. Instead, he highlighted a Marine Corps that will also battle in ones and zeroes. He portrayed the Corps as in the middle of a digital battle, “in phase 2.5 against potential countries and adversaries,” an apparent reference to different stages of combat.Canada announces controversial new cyber strategy
By: Justin Lynch
/arc-anglerfish-arc2-prod-mco.s3.amazonaws.com/public/UPBC4YGUR5FU3FGM3YCDVXGM4Q.jpg) The Canadian government has created a cyber operations center, one element of the country’s new National Cyber Security Strategy. The Canadian Center for Cyber Security will be the authority for the government’s response on digital protection for the country’s critical infrastructure, as well as its public and private sectors, according to a June 12 statement.
The Canadian government has created a cyber operations center, one element of the country’s new National Cyber Security Strategy. The Canadian Center for Cyber Security will be the authority for the government’s response on digital protection for the country’s critical infrastructure, as well as its public and private sectors, according to a June 12 statement.
“The Cyber Centre will be outward-facing, open to collaboration with industry partners and academia, as well as a trusted resource for faster, stronger responses to cyber security incidents,” said Scott Jones, who was appointed head of the body. The Canadian government also announced a new National Cybercrime Coordination Unit and a voluntary cyber certification program to help businesses understand digital threats.
The Fourth Industrial Revolution needs a social revolution, too. Here's how we can make this happen
The industrial revolution produced an explosion in new forms of social organization. From the United Nations to trades unions, from the voluntary sector to welfare states, new systems and partnerships were designed to ease the transition from one socio-economic order to the next. But today, across the globe, these organizations find themselves out of step with modern challenges and expectations. The Fourth Industrial Revolution requires a sibling social revolution. How can we make this happen? First, we must stop our expensive attempts to manage the problems better. Then we must start, with communities and professionals, to design something new. This is what I have been doing across Britain, with people like Anne.
'The Perfect Weapon' Tells The Story Of Growing Cyber War That The U.S. Is Fighting
This week, we've heard a lot about what was discussed at the summit between President Trump and North Korean leader Kim Jong Un - nuclear weapons, military exercises, returning the remains of U.S. troops killed in the Korean War. As David Sanger filed his stories from Singapore, he noticed something very big missing. Sanger is a national security correspondent for The New York Times whose new book is all about cyberweapons. DAVID SANGER: Cyber is not included in any of these discussions with North Korea. They want to do nuclear, bio, chem. And yet cyber is the only weapon that they've actually used against us and used effectively. SHAPIRO: North Korea used cyberweapons against the U.S. in the 2014 hack of Sony Pictures to catastrophic effect. And Sanger's book describes a raging cyber war happening just below the surface of public perception. The U.S. and Israel attack Iran. Russia and China attack the U.S. Sanger's new book is called "The Perfect Weapon." One story he tells in detail is about the Sony hack, which began with North Korea getting upset over a movie called "The Interview" about two journalists who plot to kill Kim Jong Un.
Assessing what state institutions can do to combat cyberattacks
 When a cyberattack has been orchestrated by a state actor, people may be tempted to call it "war". After all, it's an attack waged on national infrastructures by a foreign power. But the term "cyber war" has been used so often for dramatic effect that I don't just want to warn against hype. It's also time to dampen expectations regarding the scope of governmental intervention. Defined during the Cold War as protection against classical military threats and the defence of national territory, the term "security" is now widely understood to include non-military dimensions. Switzerland's 2016 Security Policy Report, for instance, lists not only armed attacks but also terrorism, crime, manipulation of information space, supply disruptions and disasters and emergencies as threats. This has led to security policy instruments being adapted for the prevention, defence and management of these threats. And although the military is still important here, it is no longer the only instrument.
When a cyberattack has been orchestrated by a state actor, people may be tempted to call it "war". After all, it's an attack waged on national infrastructures by a foreign power. But the term "cyber war" has been used so often for dramatic effect that I don't just want to warn against hype. It's also time to dampen expectations regarding the scope of governmental intervention. Defined during the Cold War as protection against classical military threats and the defence of national territory, the term "security" is now widely understood to include non-military dimensions. Switzerland's 2016 Security Policy Report, for instance, lists not only armed attacks but also terrorism, crime, manipulation of information space, supply disruptions and disasters and emergencies as threats. This has led to security policy instruments being adapted for the prevention, defence and management of these threats. And although the military is still important here, it is no longer the only instrument.Plenary highlights: migration, drones, Parliament's composition
From stricter drone rules to migration and the new composition of the Parliament: check out our overview of June's plenary session in Strasbourg. On Wednesday MEPs approved a proposal to reduce the number of Parliament seats from 751 to 705 after the UK leaves the EU, leaving room for new countries that may join in the future. Discover more facts about the distribution of seats in our infographic. MEPs criticized the new Italian government’s refusal to allow a boat carrying migrants, the MS Aquarius, to dock in the country, during a special debate on Wednesday and during talks about the EU summit on 28-29 June on Tuesday. MEPs called on EU leaders to come up with real solutions to finally end the migration crisis.
What the End of Net Neutrality Actually Means
What the Interwar Years Say About the US Army’s Newest Force Concept
BY LAUREN FISH
 You fix the roof when it’s sunny, says U.S. Army Secretary Mark Esper, pointing to his service’s various efforts to improve doctrine and gear during a relative lull in fighting. The Army has more funds and a clear strategy for new vehicles and equipment, the two-year-old Rapid Capabilities Office, and a brand-new Futures Command. Most interestingly, it has a new operating concept dubbed Multi-Domain Operations. Intended to advance combined arms concepts into all the domains of 21st-century war, the MDO envisions new ways the services should jointly operate, identifies new battlefield requirements, and responds to possible pitfalls in the current way the Joint Force does business. Even the name — recently changed from “multi-domain battle” — reflects the notion that future conflicts will feature forms of competition far removed from traditional kinetic combat.
You fix the roof when it’s sunny, says U.S. Army Secretary Mark Esper, pointing to his service’s various efforts to improve doctrine and gear during a relative lull in fighting. The Army has more funds and a clear strategy for new vehicles and equipment, the two-year-old Rapid Capabilities Office, and a brand-new Futures Command. Most interestingly, it has a new operating concept dubbed Multi-Domain Operations. Intended to advance combined arms concepts into all the domains of 21st-century war, the MDO envisions new ways the services should jointly operate, identifies new battlefield requirements, and responds to possible pitfalls in the current way the Joint Force does business. Even the name — recently changed from “multi-domain battle” — reflects the notion that future conflicts will feature forms of competition far removed from traditional kinetic combat.
Subscribe to:
Comments (Atom)