By SYDNEY J. FREEDBERG JR.
 In a world where knowledge increasingly matters more than physical power, US troops can’t quickly access vital information in a labyrinth of often incompatible and inaccessible databases. The Joint Enterprise Defense Infrastructure — archly acronymized as JEDI — aims to fix all that. A soldier from the Army’s offensive cyber brigade during an exercise at Fort Lewis, Washington. UPDATE with Dep. Sec. Shanahan remarks PENTAGON: The Defense Department’s 10-year, $10 billion cloud computing contract isn’t just a huge information technology initiative. It’s also a weapon system.
In a world where knowledge increasingly matters more than physical power, US troops can’t quickly access vital information in a labyrinth of often incompatible and inaccessible databases. The Joint Enterprise Defense Infrastructure — archly acronymized as JEDI — aims to fix all that. A soldier from the Army’s offensive cyber brigade during an exercise at Fort Lewis, Washington. UPDATE with Dep. Sec. Shanahan remarks PENTAGON: The Defense Department’s 10-year, $10 billion cloud computing contract isn’t just a huge information technology initiative. It’s also a weapon system.
As plans stand now, JEDI will include ruggedized, miniature servers — small enough to fit in a Humvee or, in some models, even a soldier’s backpack — to ensure frontline forces can quickly access all the data in the network. Larger versions of these “tactical edge computing devices” will go on ships or fit in shipping containers to form “rapidly deployable data centers” in combat zones, said Tim Van Name of the Defense Digital Service. Van Name called me from Irbil, Iraq, where he was inspecting current battlefield tech.
As a result, JEDI will give frontline warfighters the kind of information once reserved for generals, Brig. Gen. David Krumm of the Joint Staff told me. “We need to make sure we understand information is no longer only reserved for senior leaders to make decisions and then provide orders to the soldier, sailor, marine, airman on the battlefield,” Krumm said. “It’s for those people on the battlefield to have the information to make the right decision.
The problem is the Defense Department’s information technology is historically set up to serve big headquarters and Pentagon agencies, each with its own in-house servers and mainframes. The intelligence community has already moved away from this disjointed model to a unified cloud called ICITE, in which different organizations rely on a single common provider of data storage and computing power. (Gmail is probably the most common cloud application: Your emails are stored on Google’s servers instead of on your own computer or your company’s).
The Department of Defense has tried to adopt cloud computing. But instead of replacing its fragmented infrastructure with a single common cloud that all can share, DoD’s just ported its fragmentation to the cloud.
“In DoD, we have over 500 cloud applications right now, and they don’t all talk to each other,” Krumm said. “What we have to have is a way to integrate all of that. The JEDI cloud is our first initiative to try to do that.”

Knowledge (Shared) Is Power
So in a world where knowledge increasingly matters more than physical power, US troops can’t quickly access vital information in a labyrinth of often incompatible and inaccessible databases. You can get the information eventually, but it generally requires asking a human being with access to the desired database to find it for you, convert it into something you can access, and send it along. That’s a vastly slower process than the frontline user just accessing the data directly.
It also makes it impossible to use cutting edge techniques in artificial intelligence, machine learning, and big data analysis, which require giving algorithms access to large amounts of data. Industry has developed great tools to manage masses of information, Van Name said, but they won’t work on the Defense Department’s existing, fragmented infrastructure.
The Joint Enterprise Defense Infrastructure — archly acronymized as JEDI — aims to fix all that. Instead of the Force in Star Wars, which connects individual warrior-sages to the power of the cosmos, JEDI will connect individual combat troops, officers, intelligence analysts, and others to a wider universe of information.
The bottom line for warfighters? “They’ll be able to make more informed decisions,” Krumm said, especially with the aid of artificial intelligence. “When we look at AI machine learning, what we’re really talking about is the ability to glean information from what is a massive amount of data, coming from all sorts of sources, that gives us the advantage in making decisions really quickly.”
“When you have the information available globally, it creates all sorts of new possibilities for the warfighter to realize it,” he went on. With cloud connectivity providing data to frontline forces, he said, “it might go directly to an F-35, it might go directly to an M1 Abrams tank, it might to go a submarine…..As we go towards some of the new innovative technologies (like) autonomy, unmanned vehicles, the availability and accessibility of this data will drive effectiveness of those machines as well.”
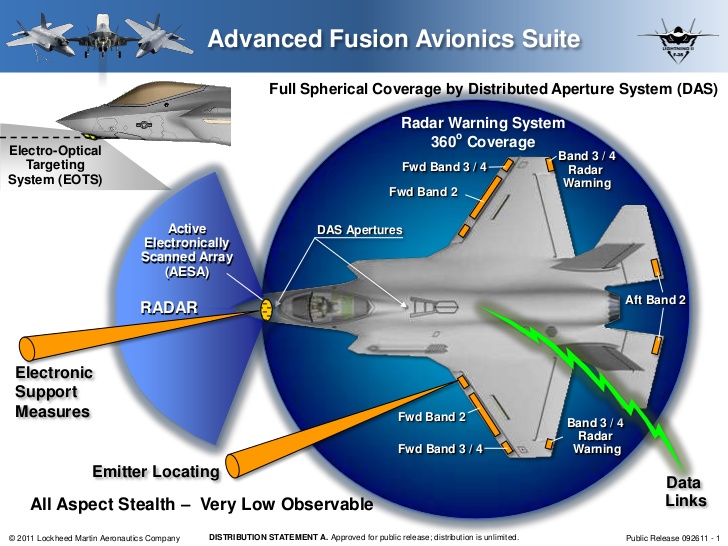
F-35 sensors
Grand Ambitions
All this sounds ambitious — and when the government tries an ambitious information technology program, it rarely ends well. The JEDI contract has already come under heavy criticism, particularly over its call for a single winner-take-all contract award, a provision which has survived revisions of the Request For Proposal: Most big companies rely on several cloud providers as insurance against any one going down. Congress has ordered the Defense Department to explain its reasoning.
The Pentagon, for its part, emphasizes that the initial JEI contract is only two years, only reaching the full 10 years (and an estimated $10 billion value) if all options are exercised — giving plenty of opportunities, in theory, to jettison an unsatisfactory contractor.
UPDATE: Deputy Secretary of Defense Patrick Shanahan told reporters Tuesday morning that the Pentagon will only allow offices to switch to the Cloud if they first commit to shuttering all of the legacy systems where they have been hosting data. He also said that his time in the defense industry showed him the value of competition and emphasized there’ll be a full and open competition for the JEDI Cloud contract among multiple vendors, not a sole-source award. “Two is better than one, and three is better than two,” he told the Defense Writers’ Group. “This is about preserving options.”
For all JEDI’s controversial ambitions, however, it’s important to understand what is not trying to do. It’s not trying to reinvent the wheel, in two different ways: It’ll rely on existing military communications systems to carry the data, and it’ll rely on existing commercial software to handle the data.
The military already has a vast network of tactical radios, communications satellites, command posts, and so on. JEDI will use them, not replace them, Van Name emphasized, and even rely on them for much of its security. “It will rely on the significant transport capabilities that the department already has,” he told me. “The applications themselves will still need to be secure, (but) the underlying infrastructure is pretty hardened, and that’s a great thing for the department.”
Meanwhile, the commercial world has invested heavily in the software to manage a cloud and analyze masses of data. Whichever company wins the JEDI contract will take its commercial offerings and “replicate those services in their entirety for use in the classified space,” Van Name said.
JEDI also plans to tap into ongoing commercial software development cycles to keep the cloud up to date. If the military needs an application that exists in the commercial world but not in the military cloud, the JEDI contractor can simply port that existing app from the unclassified world to the secure network, rather than reinvent it from scratch.
“I don’t want to measure requirements in months,” Krumm told me. “As opposed to…going through months of acquisition, we’re hoping days or maybe even hours of being able to go into JEDI, get the services we need, and start.”
No comments:
Post a Comment