BY BRAHMA CHELLANEY
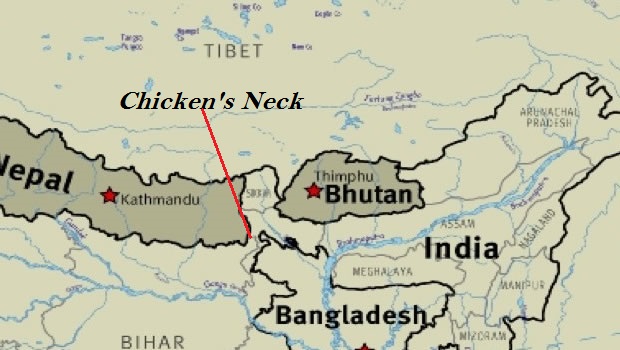

Bhutan, one of the world’s smallest nations, has protested that the Asian colossus, China, is chipping away at its territory by building a strategic highway near the Tibet-India-Bhutan trijunction in the Himalayas. Bhutan has security arrangements with India, and the construction has triggered a tense standoff between Chinese and Indian troops at the trijunction, with the Chinese state media warning of the possibility of war.
Bhutan says “China’s construction of the road inside Bhutanese territory is a direct violation” of its agreements with Beijing. China, however, has sought to obscure its aggression by blaming India for not respecting either the trijunction points or the boundary between Tibet and the Indian state of Sikkim, which is also contiguous to Bhutan.