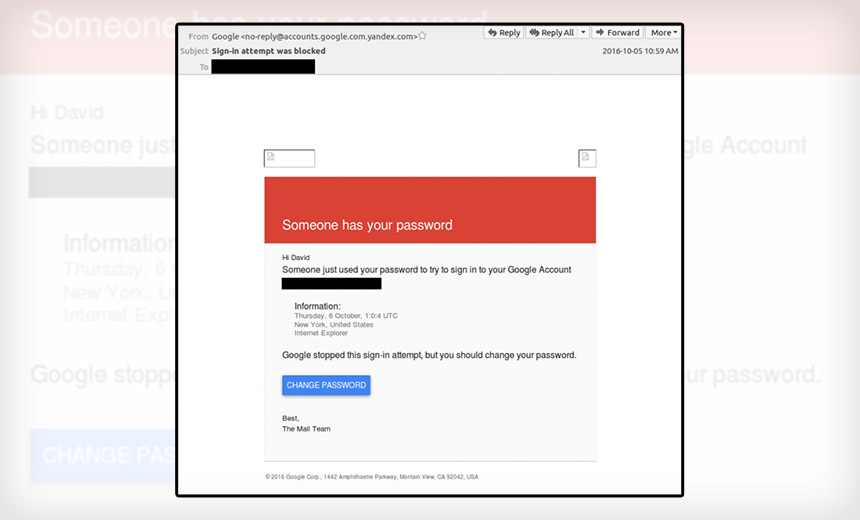
A phishing email sent to one of the victims of the cyber-espionage campaign. (Source: Citizen Lab)
A "single cyber espionage campaign" apparently linked to Russia has targeted more than 200 people in 39 countries with phishing attacks, according to privacy researchers at University of Toronto's Citizen Lab.
The researchers say many of the phishing attacks employ fake - but real-looking - emails from Google, and that successful attacks have resulted in the theft and dumping of documents from victims' Google Drive accounts.
Some of the dumped documents have first been altered before being released as part of a parallel disinformation campaign, the Citizen Lab researchers write in a new report, Tainted Leaks: Disinformation and Phishing With a Russian Nexus.
Individuals known to have been targeted by attackers include members of 28 governments, as well as a former Russian prime minister, ambassadors, senior military officers and heads of energy companies. The attackers have also targeted "academics, activists, journalists, and representatives of non-governmental organizations," the researchers say.
Citizen Lab's research builds on - and acknowledges - extensive work that has been done by security researchers at such firms as Dell Secureworks, FireEye's Mandiant and ThreatConnect to trace the infrastructure and tactics used by allegedly Russian cyber-espionage attackers (see No Shock: Russia Confirms 'Cyber War' Efforts).
Citizen Lab says its "patient zero" in these attacks - which led to them becoming aware of and unraveling the much larger phishing campaign - was investigative journalist David Satter. He regularly reports on Russia and was banned from the country in 2013 because of his reporting.
Fast-forward to October 2016, when Satter fell victim to a phishing attack targeting his Gmail credentials. "Documents stolen from his account then appeared on the website of CyberBerkut, a self-described pro-Russian hacktivist group," Ronald Deibert, director of the Citizen Lab - part of the Munk School of Global Affairs at University of Toronto - says in a blog post. He co-authored the report with Citizen Lab researchers Adam Hulcoop, John Scott-Railton, Peter Tanchak and Matt Brooks.
The researchers' previous investigations have revealed software exploits as well as spyware used by governments with questionable human rights records to monitor activists and dissidents.
Disinformation Campaign
With Satter's consent, Citizen Lab says it compared genuine documents provided by Satter with what was released, some of which turned out to have been altered or faked.
"Our report details the disinformation campaign that was orchestrated around his stolen emails to give the false impression that Satter was part of a CIA-backed plot to discredit Putin and his adversaries and engineer a 'color revolution,'" Deibert says. "The disinformation was also aimed at providing a false association between Satter, western NGOs, and prominent Russian opposition figures, most notably the prominent Russian anti-corruption activist, Alexei Navalny."
Studying the attack against Satter, the Citizen Lab researchers say they found that Tiny.cc, a legitimate link-shortening service used by the attackers to make it appear that their emails had come from Google, had "predictable features that enabled us to discover some other links likely used by the same operators." All told, the researchers recovered 223 malicious links that appeared to be used to target 218 individuals, 85 percent of which the researchers believe they have traced to real identities.

Some of the phishing links discovered by researchers as they traced back Tiny.cc shortcodes. (Source: Citizen Lab)
The researchers say they attempted to notify victims, taking into account some considerations. For example, if victims were part of a government organization, the researchers notified that country's national computer emergency response team. Likewise, if targets shared an affiliation with an organization - but not a single employer - then they attempted to work with the organization to notify the individuals.
Difficult Detective Work
Other researchers with experience unraveling Russian cyber espionage and disinformation efforts have lauded Citizen Lab's research into this phishing campaign.
Thomas Rid, a professor of war studies at King's College London, praised the researchers for their "extraordinary detective work" via a Twitter post. "The Tiny.cc reversing and discovery is simply stunning. Huge respect."
Targets in 39 Countries

Source: Citizen Lab
Ties to DNC, Podesta Phishing
The Citizen Lab researchers are careful to offer caveats about their findings, saying they have "no conclusive evidence that links these operations to a particular Russian government agency," while noting that there are clear areas of overlap between their findings and other researchers' discoveries.
"This overlap includes technical details associated with the successful breach in 2016 of the email account of John Podesta, the former chairman of Hillary Clinton's unsuccessful presidential campaign," Deibert says.
In July 2016, Dell Secureworks published a report attributing the hack of Podesta's Gmail account - as well as other attacks against the Democratic National Committee - to cyber-espionage hackers who appear to be tied to the Russian government. The group is known as Fancy Bear, aka APT28, Pawn Storm, Sednit, Sofacy, Strontium and the Tsar Team.
U.S. intelligence agencies in January, meanwhile, issued a report saying that Podesta was one of a number of victims of phishing campaigns launched as part of a broader Kremlin effort to influence the 2016 U.S. presidential election (see Russian Interference: Anatomy of a Propaganda Campaign).
Some of Podesta's emails ended up being published on DCLeaks.com and on a WordPress site authored by Guccifer 2.0 - a persona that U.S. intelligence agencies believe was concocted by Russian intelligence. WikiLeaks later received the emails and published them as well.
No comments:
Post a Comment