by Gavin Larsen
 The Australian Prime Minister, Malcolm Turnbull, recently warned that all Australians should be concerned about the threat of a cyber-attack. Mr Turnbull described cyber warfare as the new frontier, with families, governments and businesses equally at risk.
The Australian Prime Minister, Malcolm Turnbull, recently warned that all Australians should be concerned about the threat of a cyber-attack. Mr Turnbull described cyber warfare as the new frontier, with families, governments and businesses equally at risk.
From a public perspective, there is a greater expectation placed on the government to ensure that the networks used by their citizens (to provide sensitive information) are secure and protected from cyber-attacks. Similarly, national security remains a critical requirement for governments.
The Prime Minister is right to declare cyber warfare as the new frontier; especially for governments.
An increased focus by hackers on Governments was reported by Radware in its 2015-2016 Global Application & Network Security Report. Those findings have been substantiated in Radware’s recently released 2016–2017 report.
The report found that there had been a significant increase in attacks against governmental institutions bringing a new level of politically affiliated cyber protests. While the U.S. presidential election was in the spotlight, the media reported on a different breach almost weekly. Australia was not immune with attacks on Australian Government agencies also being reported across the globe.
While some may have taken offense that the Prime Minister had publicised issues relating to attacks against Australian Government agencies, there is a difference between calling out agencies with their specific vulnerabilities and undertaking vulnerability research.
For example, if the PM had stated: “The Department of Energy, primary nuclear reactors are vulnerable at the Siemens PLC controllers for this new attack that can be launched by attacking this vector (without disclosing to Siemens the vulnerability and giving them time to patch and announce), that could be interpreted as irresponsible.
There are many places around the world that are vulnerable and the most proactive method of securing these vulnerabilities can be achieved by focusing on them and fixing them. Many companies around the world now pay Bug Bounties or crowdsource their vulnerability findings. They have determined that “hiding” from vulnerabilities will only stop the attacks from happening for so long. This accords with the Prime Minister’s comment that “you can pretend the threats are not there, if you like, but that will only make you susceptible to being taken in by them.”
A recent example in support of this is United Airlines. After some speculation that Airlines were at risk in the US, there was at first a knee jerk reaction that ‘any’ findings were considered criminal but after some time, airlines opened up to crowd sourcing and now offer bug bounties.
Top-Level Findings from Radware’s 2016-2017 Global Application & Network Security Report
98% of Organizations Experienced Attacks in 2016:
Cyber-attacks became a way of life for nearly every organization in 2016. It is Radware’s view this trend will continue in 2017.
IoT Botnets Open the 1TBps Floodgates:
This exemplifies why preparing for “common” attacks is no longer enough. This event introduced sophisticated vectors, such as GRE floods and DNS water torture.
Cyber-Ransom Proves Easiest, Most Lucrative Tool for Cybercriminals:
Almost all ransom events have a different attack vector, technique or angle. There are hundreds of encrypting malware types, many of which were developed and discovered this year as part of the hype. Also, DDoS for ransom groups are professionals who leverage a set of network and application attacks to demonstrate their intentions and power.
Cyber-Attacks Cost Almost Twice What You May Think:
Most companies or government agencies have not come up with a precise calculation of the losses associated with a cyber-attack. Those who have quantified the losses estimate the damage at nearly double the amount compared to those who estimate.
Stateful Devices: #1 Point of Failure:
Common IT devices, including firewalls, application delivery controllers and intrusion protection systems, now represent the greatest risk for an outage. Consequently, they require a dedicated attack- mitigation solution to protect them.
Threat Landscape Trends
In addition to a significant increase in attacks against governmental institutions, the 2016-2017 report also identified the following Threat Landscape Trends:
SSL-Based Attacks Continue to Grow:
Although 39% report suffering an SSL-based attack, only 25% confidently state they can mitigate it.
Data Leakage + SLA Impact Are Top Concerns:
Data leakage and service level impact often come together, with a DDoS attack serving as a smoke screen that distracts IT teams so data can be infiltrated.
Non-Volumetric DoS: Alive and Kicking:
Despite astonishing volumes, neither the number of victims nor the frequency of attacks has grown. Most non-volumetric DDoS attacks are in relatively lower volumes, with 70% below 100MBps. Rate-based security solutions continue to fall short, requiring companies to rethink their security strategy and embrace more sophisticated solutions. Without those upgrades, there is a good chance an organization will experience, yet lack visibility, into service degradation.
DDoS Attacks Are Becoming Shorter:
Burst attacks are increasing thanks to their effectiveness against most mitigation solutions.
Mirai Rewrites the Rules:
As the first IoT open-source botnet, Mirai is changing the rules of real-time mitigation and making security automation a must. It isn’t just that IoT botnets can facilitate sophisticated L7 attack launches in high volumes. The fact that Mirai is open-source code means hackers can potentially mutate and customize it— resulting in an untold variety of new attack tools that can be detected only through intelligent automation.
Radware’s 2016-2017 Global Application & Network Security Report findings are from a 2016 security industry survey; reflect Radware’s Emergency Response Team’s (ERT) “in-the- trenches” experiences fighting cyber-attacks and incorporates perspectives of third-party service providers. This research provides a comprehensive and objective review of 2016 cyber-attacks from both a business and a technical perspective. It also offers best practices for organizations to consider when planning for cyber-attack protection in 2017.
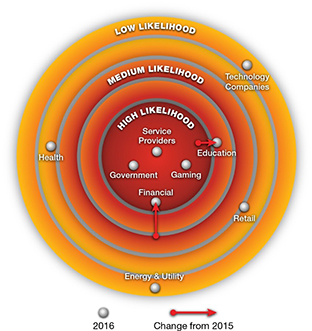
Radware’s Cyber-Attack Ring of Fire
The Cyber-Attack Ring of Fire maps vertical markets based on the likelihood that organizations in these sectors will
experience cyber-attacks. The Ring of Fire reflects five risk levels. As sectors move closer to the red center, such organizations are more likely to experience denial-of-service and other cyber-related attacks at a higher frequency than the others.
There have been changes to the Ring of Fire since last year. Telecom, government institutions and gaming companies stay at the center of likelihood while the financial services industry has moved toward the center. Retail, education and healthcare industries remain stable, but technology companies are actually moving away from the center. Energy and utility companies remain in the low risk level due to tighter security.
No comments:
Post a Comment