August 22, 2016
 The U.S. National Security Agency was apparently able to decrypt any traffic sent using a Cisco PIX device that was built from at least 2002 to 2008. While Cisco stopped supporting PIX devices in 2013, more than 15,000 remain in use and are still vulnerable to related exploits.
The U.S. National Security Agency was apparently able to decrypt any traffic sent using a Cisco PIX device that was built from at least 2002 to 2008. While Cisco stopped supporting PIX devices in 2013, more than 15,000 remain in use and are still vulnerable to related exploits.
Those findings come via security researchers who continue to pore over the 250 MBEquation Group data dump from Aug. 13, which contains a bevy of firewall attack tools. The tools are designed to compromise devices built by Cisco, Fortinet, Juniper and Topsec (seeEquation Group Stings Firewall Vendors with Zero-Day Flaws).
Based on security researchers' teardowns of the tools, as well as an NSA malware manualreleased Aug. 19 by the Intercept - via documents provided by former NSA contractor Edward Snowden - there is widespread agreement that the tools were built by the NSA. But the identity of the Shadow Brokers remains a mystery.
Cisco has confirmed that two vulnerabilities exploited via the dumped tools were legitimate and could be exploited by tools named EXTRABACON and EPICBANANA. The former exploited a zero-day flaw, which Cisco has patched, while the latter targeted a flaw that Cisco patched in 2011. Fortinet has also patched an update for a flaw contained in the dump, and Juniper says it's continuing to review the data dump.
But in recent days, researchers have made a new discovery: An exploit called BENIGNCERTAIN allowed the NSA to decrypt any traffic being handled by Cisco PIX devices - including devices set to function as VPNs - from at least 2002 to 2008, according to security researcher Mustafa Al-Bassam, who has been cataloging "exploits, implants and tools for hacking firewalls" that are contained in the 250 MB Equation Group dump.
In a blog post, he says the exploit appears to allow an attacker to extract private VPN keysfrom a vulnerable PIX device simply by sending it Internet Key Exchange packets designed to cause the device to dump some of its memory. "The memory dump can then be parsed to extract an RSA private key and other sensitive configuration information. That's huge," he says via Twitter.
Security researcher Brian Waters has tested BENIGNCERTAIN on Cisco hardware and found that it works up to at least version 6.3(5)145.
Cisco Confirms Some PIX Devices Vulnerable
In light of those findings, Cisco's security team issued an Aug. 19 blog post confirming that PIX versions 6.x are affected by BENIGNCERTAIN, while PIX versions 7.x and the ASA series are not.
Cisco stopped supporting all PIX hardware in 2013; it's been considered "end of life" since then.
"Our investigation so far has not identified any new vulnerabilities in current products related to the [BENIGNCERTAIN] exploit," Omar Santos, principal engineer of Cisco's Product Security Incident Response Team, says in the blog post. "Even though the Cisco PIX is not supported ... out of concern for customers who are still using PIX we have investigated this issue and found PIX versions 6.x and prior are affected. PIX versions 7.0 and later are confirmed to be unaffected by BENIGNCERTAIN. The Cisco ASA is not vulnerable." But Cisco ASA devices have been vulnerable to EPICBANANAS and EXTRABACON.
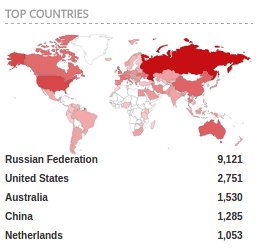
Unearthing a historical flaw that shows how the NSA may have enjoyed persistent access to any PIX device for 11 years or more is worrying. But so is the prevalence of still-deployed - and no longer supported - PIX devices. Al-Bassam, for example, counts 15,000 PIX devices - including 9,000 in Russia and nearly 3,000 in the United States - that are online and vulnerable to BENIGNCERTAIN.
There's actually over 15,000 Cisco PIX firewalls online today vulnerable to BENIGNCERTAIN, most of them in Russia.
PIX Devices Power Botnets
Some of those vulnerable PIX devices in Pakistan have been used by other attackers to help build three botnets, including a botnet comprised of 1,700 devices infected by Kaiten.c, an IRC-based distributed denial-of-service attack tool, Al-Bassam says. "Whoever owns this botnet, they seem to have owned an entire department of the Pakistan government: the Pakistan Software Export Board," he says. "Most likely someone is compromising Cisco firewalls to grow their botnet."
The PIX devices continue to remain vulnerable to the exploited flaw, and Cisco has given no indication that it plans to release a PIX patch.
The bot is actually kaiten.c. Most likely someone is compromising Cisco firewalls to grow their botnet. ht @info_dox
Someone compromising Cisco PIX routers has managed to grow a botnet of 1700 bots. pic.twitter.com/cOmjZYxa15
The ability to remotely intercept and decrypt traffic from Cisco VPNs and firewalls offered the NSA the equivalent of "Internet god mode," according to "Hacker Fantastic," which is the handle of a white hat hacker who works for U.K. consultancy MDSec. "God mode" is videogame-speak for cheat code that allows players to gain invincibility as well as go anywhere and do anything in a game, including walking through walls.
Anyone calling NSA exploits released lame has literally 0 clue value of such code. Remote unauth'd cisco PIX & ASA code is Internet god mode
After Snowden Leaks, Fresh Exploit Questions
The existence of BENIGNCERTAIN is certain to prompt tough questions for the U.S. government and its approach to searching for - and weaponizing - exploits for hardware and software built by major vendors, including U.S. manufacturers.
"What is a company supposed to do when the very technology that they bought to protect them makes them vulnerable?" Jeff Pollard, a principal analyst focused on IT security at Forrester Research, asks The Washington Post.
Already, some security watchers have called on the U.S. government to more quickly release details of vulnerabilities that it finds to manufacturers.
But Robert David Graham, who heads offensive security research firm Errata Security, notes that exploits don't grow on trees; intelligence agencies go hunting for them and oftentimes develop them with specific uses in mind. In a blog post, he notes that there can be legitimate uses for exploiting these flaws - such as hacking into a terrorist network - which complicates the vulnerability-disclosure discussion.
"There are legitimate policy questions about government hacking and use of [zero] days," Graham says, while adding that he would like to see the government more clearly articulate how and when it uses such exploits. "At the bare minimum, there should be more transparency."
No comments:
Post a Comment